The WannaCry ransomware attack was the attack of network worm which used leaked NSA exploit and was
nicknamed WannaCry (other names include WannaCrypt, WanaCrypt0r 2.0,] Wanna Decryptor). The work targeted
all version of Microsoft Windows with SMBv1 protocol enabled. Like Cryptolocker
Trojan before it encrypt user data with a predefined, fixed set of extensions (see below) and then
display informational screen demanding ransom payments in bitcoins. The message is translated in more
then twenty languages, so the author expected the global scale of the attack.
Looks like the code of the wor Microsft went as far as proposing Geneva convention for goverment, in order
to stop them from stockpiling exploits for its OS The
New York Times, May 14, 2017):
The attack started around 10 AM GMT Friday, 12 May 2017 and has been described as unprecedented in
scale, infecting larger number on computers in GB (where National Health service was hit hard) and other
other countries. The total number estimate vary from 70K to more than 200K computers in over one hundred
countries. The worst-hit countries and organization are countries with substantial presence of Windows
XP on computers. They include mostly xUSSR countries, China, India, Japan and other South-eastern
countries. Among the organizations hit, universities and medical institutions probably suffered
most, as they still use Windows XP, especially in the countries mentioned above.
While CryptoLock relied for propagation distribution of phishing emails in case of WannaCry
this method of attack has not been confirmed. It might well be that this is pure netwrk worm.
Once installed, WannaCry uses the EternalBlue exploit and DoublePulsar backdoor developed by the NSA
to spread both in local networks and Internet connected PC (generating random addresses for probing
them). Only PCs which have not been updated with the security updates released by Microsoft on 14 March
2017 .
This time we were simply lucky. Wanna Cry worm contains the kill switch which was discovered accidentally,
activated in the afternoon on May 12, 2017 and which prevented epidemics spreading after May 12. So
most infections happened on May 12 from approximately 10 AM when the work was released until the kill
switch was activated (let's say 6 PM). That means that the most damaging period was only 8 hous long
or so. 10 AM GMT is night in the USA and most of LA so, they were double lucky). Looks
like the switch is primitive measure to avoid wunning the work in VMs because it checks for existence
of DNS record of some very obsure name (which GB researcher registed without understand the consequnces
of this action; which proved to be highly positieve).
In newroks with a proxy kill switch was not always accecible (depends on intrnal DNS settings)
and large organizations have more problems in this respect then small organizations and home users.
That means that Wanna Cry is less dangerious for personal PCs then for corporate PCs which are connected
to internet via proxy. Looks liek the work is not proxy0-aware (which means that it is the product
of some gang, not a state-sponsored laboratory) and in this case it will spead "as usual" because DNS
lookup will fail.
This type of attack isn't new, but it's the world-wide scale still is surprising. What appeared to
be the biggest cyber extortion attack in history affecting computer in over 100 countries around the
globe. File size of the ransomware is 3.4MB (3514368 bytes). Once infected, the encrypted files
contain the file extension .WNCRYT.
Translations on the warning notice to around 20 languages are very polished, without major
grammar errors. Sophistication also seen in the command and control center: for communication
with it the malware extracts and uses Tor service executable with all necessary libraries dependencies
to access the Tor network. Depending of the method of the download that provide an opportunity to disable
the worm after it tries to launch Tor.
It started distribution on May 12, 2017. At 11 AM in GB some hospital computers were already infected.
National Health Service,
www.NHS.uk was hit hard with
this ransomware attack that demands $300 in bitcoins for each system it infects - in the NHS this could
total $500,000 USD in ransomware demands so far, due to malware propagation across more than one thousand
Windows computers. Assuming the the kill switch was activated around 6PM (somewhere
after lunch) so the whole attack probably lasted just 8-9 hours.
MalwareTech provided a map from which it is clear that a large number of organizations in the USA,
GB, Russia, India and China have been hit (
https://intel.malwaretech.com/botnet/wcrypt
). Please note that emerging dots signify attempt of infection that failed as map in based of
DMS requests to the resitered domain which serves as a kill switch for the worm.
So far the most sizable effects were in GB hospital system and they happened on May 12.
As for other countries, the situation up to May 13 was as following (estimates were derived from
various publications and might be misleading and incorrect):
Add this numbers and you have around 60K-70K computers worldwide infected in a single day. And even
with the kill switch the worm slowly continues to spread as there is a variant that does not have a
kill switch. Some site figure as high as 200K infected computers. (Times
of India ). Most of those computer contain little or no useful information are "useless"
or the one that can be restored without problem (like computer that show information in German railway).
The most dangerous case was the encryption of the data within GB hospital network.
In any case, from May 13 the worm infections are on a downward slope and real infections are extremely
few, because of "kill switch" activation and the fact that the malware is not able to connect to the
registered domain. Now about an interesting "kill switch" discovery story. Several hours after
the initial release of the ransomware on 12 May 2017, a researcher with the Twitter handle 'MalwareTech'
discovered what amounted to be a "kill
switch" hardcoded in the malware and accidentally activated it by registering the domain name.
This allowed the spread of the initial version of the worm to be halted. However, variant(s) without
the kill switch were detected the next day.
In an unusual move, Microsoft created and released on May 13 security patches for several now-unsupported
versions of Windows, including Windows XP, Windows 8 and Windows Server 2003.
The origin of this ransomware are currently unknown. As of May 14 Britain’s National Crime Agency
was still working on the determining where the attacks came from.
Unlike Cryptolocker, Wanna Cry uses network propagation. Probably exclusively. No
evidence for an initial email phishing campaign has been found in this case. For network propagation
it utilized NSA exploit called EternalBlue. The latter proved to be extremely effective (as can be expected
for NSA) taking into account the fact that patch was availbel fro two months (since March 14). Of course,
for discontinued version of Window there were no patach and that explain relatively high number infections
in Russi, India and China. For most consumers Windows XP is good enough and Windows 7 represents only
marginal improvement, which windows 8 and 10 -- one step forward, to steps back. Another aggravating
factor is that many Wndows 7 users disabled Microsoft updates due to Microsoft obnoxious campaign to
move them to Windows 10.
This exploit target Microsoft windows vulnerability in SMB v1 protocol (patched by Microsoft on March
14, 2017 in the update
MS17-010). This way the worm instance can scan the neighborhood and continue to propagate to vulnerable
computers on the local network as well as probe some random Internet addresses, creating mass infection
with the volume, unachievable then only mail attachments are used.
As it traverses the local network if probably can jump to a different but connected organization.
In this sense its behaviour is very simila to previous network worms, especially
Zotob worm. Which represented bigger problem
in organizations then in individual users space. This work aslo is more dangerous for organizations
than individuals as when it gets to internal network it continue to spread to most/all unpatched computers
and servers.
While that issue was parched in March 14, Microsoft issues additional patches on May 13 (including
patched for windows XP, Vista, Windows server 2003, and other version of Windows and Windows server
that are still in widespread use) and incorporated signatures of the worm into its antivirus products,
such as Windows Defender. Other anti virus first were also quick to issue updates.
New infections partially stopped on May 13 as the kill switch in the worm was accidentally activated.
USA is in the most beneficial position due to the time zone and probably is the least affected country.
Other countries were hit more. In GB and India serious disruptions of government organizations were
reported. Probably several thousand computers are affected. But on May 13 Slashdot reported about
vertion of the work that does not have a kill switch.
It seriously changes views on malware, antivirus programs and on backup routines. Like CryptoLocker
before it managed to get into front pages of major newspapers like
Guardian (May 12, 2017)
Like CryptoLocker before, this ransomware does not need Admin access to inflict the most damage.
And it can target data Linux servers, which are mounted via Samba as well. Data on all mapped network
drives can be encrypted. It has extensive list of extensions, so the first line of defense is to rename
you backup with the extension that is not in the list (for example your old password). If you
offload your backups to cloud storage without versioning and this backup has an extension present in
the list of extensions used by this Trojan, it will destroy (aka encrypt) your "cloud" backups too.
Which may or may not result in similar revenue for the cybercriminals.
Status of servers that the work communicated from the Command and Control is unknown. Probably some
might be already blocked; still chances are reasonably high -that at least one server the Trojan "pings"
is usually operational and decryption is possible. At the same time the three days timer is real and
if it is expire possibility of decrypting files is gone. Essentially you have only two options:
Beware snake oil salesmen, who try to sell you the "disinfection" solution. So far there is no such
tool
Like was the case with Cryptolocker AV companies were caught without pants. This time the timer of
ransomware is set to three days after which the extension sum increases, so the damage tot he customers
was greater, in comparison with the CryproLocker. The ransomware supposedly deletes the decryption key
if payment is not made in seven days.
Rebooting PC does not clear the timer. This time signatures were updated in one day which is record
time. such a prompt reaction is natural due the amount of damage caused by the worm, which proved
again that the level of protection provided by most AV programs is mostly fake. Standalone proxy
or private VPN is probably a better investment.
Microsoft definitely could do more to defect malware that uses this exploit.
Names as always vary from one AV company to another. The most typical are WannaCry or “Wanna Decryptor”,
WnCry, "Wana Crypt0r 2.0"
According to McAfee, once infected, the encrypted files contain the file extension .WNCRYT.
Other sources suggest .WNCRY. You can search for both using
If you are not yet infected and control your firewall SMB port needs to be blocked on firewall "just
in case" (port 445).
See A global outbreak of
computer extortion virus Tianjin enterprise do release letter WannaCry worm infection emergency treatment.
The main danger are dormant Windows XP VM which were unused for a long time -- lauching of those
might lea to infection. Generally percentatge of Windows XP infection anough total number of infection
might be very high although the exact number is unknown. That's why such countries as Russia, China,
India, Korea and Japan were hit so hard.
Payment typically works in such cases. According to Mcafee, WannaCry offers free decryption for some
random number of files in the folder C:\Intel\<random folder name>\f.wnry. We have seen 10 files decrypted
for free. Judging from the amount of payments made on May 12 and May 13 the number of infection of PC
with important data is extremly low (the total sum is less then $64K, nt in millions like was the case
with CryptoLock)
Consider it to be a fine for the lack of the backup. Now, after the fact it makes sense to
disable SMB v.1. But this is just Monday morning quarterbacking.
Recovery without payment means "restore from the backup". That means that the most viable defense
path is to use Linux computer for backups, transferring them via ssh (rsync) or FTP.
Valuable dynamic data are usually very small subset of the total amount of your data. Such data should
be separate on a small, 32GB or 64 Gb partition which is quick to backup. 32GB partition backup via
USB3 connected and just three-five minute. There is no reason not to do it the first thing in
the morning while drinking your morning coffee or tea. You should have at least two backup drives
and change them weekly so that in worst case you have your week old data available. Most people can
survive the loss of one week of data.
Another viable defense path is installing more strict group policies, blocking executables in your
Documents and Settings folder and enforcing strong software restriction policies
(SRPs) to disallow the executing of .exe files from AppData/Roaming as well as %AppData%\*\*.exe.
See Prevention for some ideas of creating such group policies.
It also stressed the value of daily cold backups, good spam filter and filtering executable attachments.
From now on backup files should be renamed with the unique extension (your old password is OK)
so that they were not affected by the work.
Paying ransom does not guarantee that you will get your files back, only cold backup does
As servers used by this ransomware will not be touched by law enforcement until the dust settles,
chances that you can decrypt you data by paying ransom are high but not 100%.
Wanna Cry does not affect Acronis backups and other rare backup programs. In this case restoration
is pretty straitforward. But this is just an accident. New variants/copycats can well target those
extensions too.
System restore point is not a REAL option. It keeps the files encrypted, it only restores to a point
where the files of the malware was not present on the system. The ghostexplorer only works
IF you have shadowcopy functionality and have it turned on. That means you do not have the shadowcopy
turned on and you do a system restore, the files are lost, paying for the decryption after a system
restore is not possible anymore.
The only good possible way to prevent dataloss is to have a BACKUP on USB drives or flash drives
make dayly so you can restore that data one day before the infection.
There are only two options for recovering encrypted files, and they all rely on either having System
Restore/VSS turned on or having a backup disconnected from the infected machine. Undelete software doesn't work as it encrypts the files in place on the hard drive, there is no copying
going on.
Infection vectors are unclear but probably there no evidence that mail attachments used. Probably
NSA exploit using SMBv1 oe SMB v2 (it is unclear -- Kaspersky mentions SMB v2) was the main
attack vector for this worm, which allowed the work to spread to SMB filesystems worldwide (WannaCry
ransomware used in widespread attacks all over the world - Securelist )
Microsoft Windows vulnerabilities are big business now, so the exploit used can be replaced by another,
as soon as a new exploit is leaked.
There are at least two variant of this worm: one with the kill switch (checks if DNS record
exists for a specific domain) and the other without. It is unlearn what other differences are.
The work appends .WCRY to the end of each encrypted file. According to Semantic the list
of extensions used by this worm include the following extensions.
Unlike most Trojans this one does not Admin access to inflict the most damage. After computer is
infected all malware needs is the write access to the files (in this case it tried to enforce
it) for this particular work restricting the port 445 on your firewall is the measure to attempt
first. But this is particular worm specific measure and it probably will not work for the
next generation of ransomware. Still this is a very important measure, especially if you have dormant
Windows XP VMs on you PC. Of course you need to patch them but this measure prevent their infection
in the first place.
Here are some more generic ideas of proactive prevention of this and similar ransomware:
There is no reason for example to allow your computer/laptop to connect to network printers outside
your local network. You can also tighten setting using Microsoft provided interface:
Windows 7 Firewall How
It Compares Against Other Firewalls.
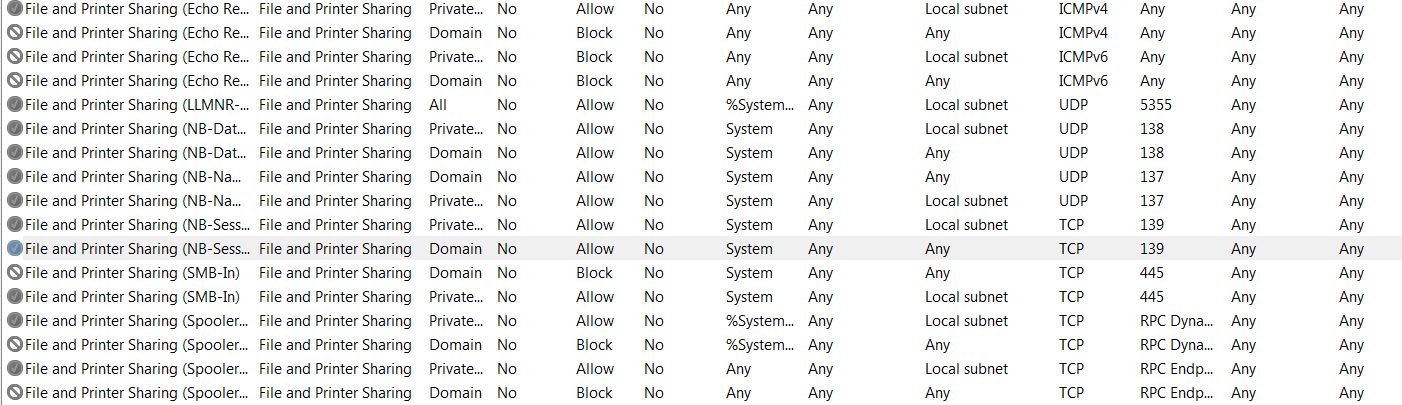
From viewing firewall rules table it is clear how insecure
Windows is and how many proprietary services enjoy unlimited connectivity. Espeailly updaters for
proriatory software, which for sure are full of security holes.
For example, why Logitech
software can connect anywhere. It should be limited to logitech.com
Also few people use remote (located somewhere on Internet) SMB services. Still it is enabled. For this worm restricting
the port 445 on your firewall is the measure to attempt first.
Also put the same "canary file" and a "huge" file in your
Documents folder as well as the directory where you store backups. You can also do the same trick
with other directories with valuable data if you have such. You may change
the name but I doubt that such worms are engaged in de-duplication business ;-)
After that write a small script, for example in Perl, which monitors the content of "canary"
file using Cygwin diff utility or something like that. Run it each 10 min or so via
scheduler. If content of canary file in any of
"watched" directories changed send email, flash alert and shutdown or halt the computer.
If yu think you need a coiuple of minutes before the shutdown, to slow the worm down you can replace "canary" files in all "other" directories with
your huge-file ( do not create a new files as directories might be scanned only once).
Elimination of free memoery, for example which launching multiple "dummy" processes
(which for exampel calculate prime numbers and store them in memory), or space on the drive also can help . If you use small
SSD as your C-drive on your laptop you can generate a dummy file so that there are no space on the
drive. That means that new file can't be written to the disk.
On desktops with thier huge harddrives this is a more difficult understating and does not make any sense,
but on 120GB SSD drive this isa very quick operation.
Unmounting the volume with backup also can help, in this sense storing the backup of
USB3 drives is preferable option (I use Unix Terminology, but yes Windows allow to put the USB
volume offline; Microsoft's own
DevCon
is the command-line version of Device Manager. See also
windows - Remove
USB device from command line - Super User).
One of the most viable methods for preventing this type of malware from running is to tighten your
Group Policy. Details may vary and depends on your level of understanding Group policies. Here is one,
reasonably simple, but effective variant that does not require other then superficial understanding
of Group Policies and was created for
CryptoLocker
Prevention
This Trojan explicitly target backups in addition to files with MS Office extensions and such (see
above). Backups now need to be protected by keeping them offline and putting online only when need arise.
Network drives should unmapped. Rotating physical disks is also a good idea.
The cyberattack that hit some 200,000 computers around the world last Friday, apparently using
malicious software developed by the US National Security Agency, is only expected to escalate and
spread with the start of the new workweek.
The cyber weapon employed in the attack, known as "WannaCrypt," has proven to be one of the most
destructive and far-reaching ever. Among the targets whose computer systems were hijacked in the
attack was Britain's National Health Service, which was unable to access patient records and forced
to cancel appointments, treatments and surgeries.
Major corporations hit include the Spanish telecom Telefonica, the French automaker Renault, the
US-based delivery service Fedex and Germany's federal railway system. Among the worst affected countries
were reportedly Russia, Ukraine and Japan.
The weaponized software employed in the attacks locks up files in an infected computer by encrypting
them, while demanding $300 in Bitcoin (digital currency) to decrypt them and restore access.
Clearly, this kind of attack has the potential for massive social disruption and, through its
attack on institutions like Britain's NHS, exacting a toll in human life.
This event, among the worst global cyberattacks in history, also sheds considerable light on issues
that have dominated the political life of the United States for the past 10 months, since WikiLeaks
began its release of documents obtained from the hacked accounts of the Democratic National Committee
and John Podesta, the chairman of Hillary Clinton's presidential campaign.
The content of these leaked documents exposed, on the one hand, the DNC's machinations to sabotage
the presidential campaign of Bernie Sanders, and, on the other, the subservience of his rival, Hillary
Clinton, to Wall Street through her own previously secret and lavishly paid speeches to financial
institutions like Goldman Sachs.
Read also: Obama Warned to Defuse Tensions with Russia
This information, which served to discredit Clinton, the favored candidate of the US military
and intelligence apparatus, was drowned out by a massive campaign by the US government and the corporate
media to blame Russia for the hacking and for direct interference in the US election, i.e., by allegedly
making information available to the American people that was supposed to be kept secret from them.
Ever since then, US intelligence agencies, Democratic Party leaders and the corporate media, led
by the New York Times , have endlessly repeated the charge of Russian hacking, involving
the personal direction of Vladimir Putin. To this day, none of these agencies or media outlets have
provided any probative evidence of Russian responsibility for "hacking the US election."
Among the claims made to support the allegations against Moscow was that the hacking of the Democrats
was so sophisticated that it could have been carried out only by a state actor. In a campaign to
demonize Russia, Moscow's alleged hacking was cast as a threat to the entire planet.
Western security agencies have acknowledged that the present global cyberattack-among the worst
ever of its kind-is the work not of any state agency, but rather of a criminal organization. Moreover,
the roots of the attack lie not in Moscow, but in Washington. The "WannaCrypt" malware employed in
the attack is based on weaponized software developed by the NSA, code-named Eternal Blue, part of
a bundle of documents and computer code stolen from the NSA's server and then leaked by a hacking
group known as "Shadow Brokers."
Read also: The End of Freedom? Secret Services developing like a Cancer
Thus, amid the hysterical propaganda campaign over Russian hacking, Washington has been developing
an array of cyber-weapons that have the capability of crippling entire countries. Through the carelessness
of the NSA, some of these weapons have now been placed in the hands of criminals. US authorities
did nothing to warn the public, much less prepare it to protect itself against the inevitable unleashing
of the cyber weapons it itself had crafted.
In its report on the global cyberattacks on Saturday, the New York Times stated: "It
could take months to find out who was behind the attacks-a mystery that may go unsolved."
The co-author of these lines was the New York Times chief Washington correspondent David
E. Sanger, who, in addition to writing for the "newspaper of record," finds time to lecture at Harvard's
Kennedy School of Government, a state-connected finishing school for top political and military officials.
He also holds membership in both the Council on Foreign Relations and the Aspen Strategy Group, think
tanks that bring together capitalist politicians, military and intelligence officials and corporate
heads to discuss US imperialist strategy.
All of this makes Sanger one of the favorite media conduits for "leaks" and propaganda that the
CIA and the Pentagon want put into the public domain.
It is worth contrasting his treatment of the "WannaCrypt" ransomware attack with the way he and
the Times dealt with the allegations of Russian hacking in the run-up to and aftermath of
the 2016 US presidential election.
There was no question then of an investigation taking months to uncover the culprit, much less
any mystery going unsolved. Putin and Russia were declared guilty based upon unsubstantiated allegations
and innuendo. Ever since, the Times, serving as the propaganda outlet of the US intelligence
services, has given the lead to the rest of the media by endlessly repeating the allegation of Russian
state direction of the hacking of the Democratic Party, without bothering to provide any evidence
to back up the charge.
Read also: Political Coverup of Iraq Atrocities
With the entire world now under attack from a weapon forged by Washington's cyberwarfare experts,
the hysterical allegations of Russian hacking are placed in perspective.
From the beginning, they have been utilized as war propaganda, a means of attempting to promote
popular support for US imperialism's steady escalation of military threats and aggression against
Russia, the world's second-largest nuclear power.
Since Trump's inauguration, the Democratic Party has only intensified the anti-Russian propaganda.
It serves both as a means of pressuring the Trump administration to abandon any turn toward a less
aggressive policy toward Moscow, and of smothering the popular opposition to the right-wing and anti-working
class policies of the administration under a reactionary and neo-McCarthyite campaign painting Trump
as an agent of the Kremlin.
SOURCE www.wsws.org
WannaCrypt may be exclusively a problem for Windows users, but the worm/virus combination could hit
a Mac user with a Boot Camp partition or Windows virtual machines in VMware Fusion, Parallels, or
other software. If you fit that bill and haven't booted your Windows system since mid-March or you
didn't receive or install Microsoft's vital security update (MS17-010) released at that time, read
on.
It's critical that you don't start up a Windows XP or later installation that's unpatched and
let it connect to the Internet unless you're absolutely sure you have the SMB file-sharing service
disabled or firewall or network-monitoring software installed that will block any attempt from an
outside connection.
Also, if you use Windows XP or a few later releases of Windows that are past Microsoft's end of
support since mid-March, you wouldn't have received the security updates that Microsoft was reserving
only for corporate subscribers
until last Friday . At that point, they made these updates generally available. If you booted
any of those systems between mid-March and Friday, you're unprotected as well.
If your Mac is on a network that uses NAT and DHCP to provide private IP addresses, which is most
home networks and most small-office ones, and your router isn't set up to connect the SMB file service
from outside the local private network to your computer (whether Boot Camp or a VM), then the WannaCrypt
worm can only attack your system from other computers on the same network. If they're already patched
or there are no other Windows instances of any kind, you can boot up the system, disable SMBv1, and
apply the patches.
If you don't want to take that chance or you have a system that can be reached from the greater
Internet directly through whatever method (a routable IP or router port mapping to your Mac), you
should disable networking on your computer before restarting into Boot Camp or launching a VM. This
is easy with ethernet, but if you're using Wi-Fi for your Windows instance, you need to unplug your
network from the Internet.
After booting, disable SMBv1. This prevents the worm from reaching your computer, no matter where
it is. Microsoft offers instructions for Windows 7 and later
at this support note . If you have a Windows XP system, the process requires directly editing
the registry, and you will want to install firewall software to prevent incoming connections to SMB
(port 445) before proceeding. The firewall approach is a good additional method for any Windows instance.
Once you've either disabled SMBv1 or have a firewall in place, you can enable network access and
install all the patches required for your release, including MS17-010.
In some cases, you no longer need SMBv1, already known to be problematic, and can leave it disabled.
If for legacy reasons you have to re-enable it, make sure you have both networking monitoring and
firewall software (separately or a single app) that prevents unwanted and unexpected SMB access.
Notable quotes:
"... Danish firm Heimdal Security warned on Sunday that the new Uiwix strain doesn't include a kill-switch domain, like the one that proved instrumental in minimising the harm caused by WannaCrypt last week, although this is subject to some dispute. ..."
"... Other researchers, including Kevin Beaumont, are also telling us they haven't yet seen a variant of WannaCrypt without a kill switch. ..."
"... Certainly the NSA should have reported it to Microsoft but they apparently didn't ... ..."
"... Implying that Windows 8, and Windows 10 are better than an unmaintained Windows XP SP3 Installation. Which can still do it's job. Probably better than those other Two numbskull OSs. Assuming Microsoft were kind enough to continue supporting it. But, alas that way only madness lay. As XP does not contain Tracker's, and (Cr)App Stores to take your Moneyz. ..."
"... It's clear the NSA intended to not inform Microsoft at all as this was part or their arsenal, a secret tool on their version of a Bat Belt. We must blame the NSA as they developed it, hoarded it and then lost control of it when it got out. This should be an example of how such organisations should not be using such methods. ..."
"... The NSA found it. Kept it secret, then lost the code due to real humans making mistakes or breaking in who discover a pot of "hacker gold" runnable and mature from the fist double click. ..."
"... In my experience with embedded systems there is nothing particularly fancy about the way the PC talks to the special hardware. There is nothing that says it can't be upgraded to say 32 bit Windows 7 or even rewritten for Linux. Much of the code is written in C or Delphi. It would take a bit of work but not impossible. ..."
"... The problem is that like Microsoft the manufacturers have moved on. They are playing with their next big thing and have forgotten about that old stuff. ..."
"... And in a few years it will all be forgotten. Nachi / Blaster anyone? ..."
"... Patching and AV inevitably often is bolting the stable door after horses gone for the first hit. Yet proper user training and proper IT configuration mitigates against almost all zero day exploits. I struggle to think of any since 1991. ..."
"... Firewalls, routers, internal email servers (block anything doubtful), all superfluous services and applications removed, no adhoc sharing. users not administrators, and PROPER training of users. ..."
"... Went to the doctor's surgery this morning. All the computers were down. I queried if they'd been hit with the malware, but apparently it was as a preventative measure as their main NHS trust has been badly hit, so couldn't bring up any records or even know what the wife's blood test was supposed to be for. Next I'm expecting the wife's hospital appt to be canceled due to the chaos it is causing. ..."
"... The answer is not to avoid Windows. It's for our so-called security agencies to get to understand that they are not supposed to be a dirty tricks department collecting weapons for use against others, but that they are supposed to work on our national security - which includes public and private services and businesses as well as the Civil Service. ..."
"... Windows 10 STILL has SMBv1 needlessly enabled by default. Should either be disabled by default or removed all together. Wonder when someone will find another exploitable weakness. Staying secure means turning off protocols you don't need. ..."
"... Instead of that, criminally stupid idots at NHS IT in the affected trusts as well as other enterprises which were hit: 1. Put these unpatchable and unmaintainable machines in the same flat broadcast domain with desktop equipment. There was no attempt at isolation and segmentation whatsoever. ..."
"... Each of these should be a sackable offense for the IT staff in question. ..."
"... Systems vendors to the NHS are borderline criminal. In pharmacy, there are only 1 of 4 mandated systems vendors you can choose. The 3 desktop based ones have so much legacy crap etc that they still only work on windows 7. They also insist on bundling in a machine to just a stupid high cost to a tech illiterate customer base - generally a cut down crappier version of something you could by uin argos for 300 quid they will charge over a grand for. Their upgrade cycles are a f**king joke and their business model makes their customers very reluctant to do so as they have fork out silly money ..."
"... Firstly, a state actor attack would be far better targeted. Stuxnet, for example, actually checked the serial numbers of the centrifuges it targeted to ensure that it only hit ones created in the right date span to impact only those bought by Iran. The vector on this attack, on the other hand, literally just spammed itself out to every available IP address that had port 445 open. ..."
"... most of the original bits of this were actually quite shittily written. Oh sure, there was a genuine bit of high-tech NSA code in there from the shadow broker leak... but there was also a fair load of primitive crap there too. It's a bit like an 16 year old came into possession of an F-16; it was destructive as hell but he didn't really know how to fly it. ..."
"... there's literally 5 different layers of my SMB's security that blocked this (patching, permissions, firewall, commercial AV, VLANs). And we're not exactly cutting-edge - just running best practice. ..."
"... In short, if this was state-backed, then the state in question would have to be somewhere like Honduras, not one of the big-league infosec powers. ..."
"... I read the Malwaretech log (excellent description of why you'd look for a nonexistent domain to determine if you're sandboxed) and thought: OK, so the virus writer should check a randomly generated domain, instead of a fixed one. That way, they can't all be registered, your virus can't be kill-switched the way this one was, and your virus can still tell if it's being run in a sandbox. ..."
"... the code is not proxy aware and the kill switch would not work in well structured environments where the only access to the net is via a configured non transparent proxy. ..."
"... In this case, knowing there are a number of nation state backed cyber defence teams looking into this... they either a) have balls big enough to need a wheelbarrow and believe that they wont get caught no matter what and cyber defence is really too hard to deliver effectively, regardless of backers. or b) that they are insanely stupid and greedy and are not following the news... ..."
"... Given that the only safe/undetected way of laundering the bitcoins will be to buy drugs or guns or other such illegal goods on the darkweb and then turn that into cash by selling it on then the perps are as you say both greedy and insanely (criminally) stupid. ..."
"... If Microsoft had an update channel for security patches only, not unwanted features and M$'s own brand of malware, people would but alot more inclined to stay up to date. ..."
"... Rumors running around that this is Deep State sponsored coming out of various cliques in intelligence agencies in retaliation for the Vault 7 leaks. ..."
15 May 2017 at 09:42, John Leyden
Miscreants have launched a ransomware worm variant that abuses the same vulnerability as the
infamous
WannaCrypt
malware .
Danish firm Heimdal Security
warned
on Sunday that the new Uiwix strain doesn't include a kill-switch domain, like the one that proved
instrumental in minimising the harm caused by WannaCrypt last week, although this is subject to some
dispute.
"As far as I know there's only been two variants (one this morn) and none without [a kill]switch,"
security researcher Dave Kennedy
told El Reg
. Other researchers, including Kevin Beaumont, are also telling us they haven't yet
seen a variant of WannaCrypt without a kill switch.
What isn't in question is that follow-up attacks based on something similar to WannaCrypt are
likely and that systems therefore really need protecting. Black hats might well create a
worm that attacks the same Windows vulnerability more stealthily to install a backdoor on the many
vulnerable systems still out there, for example.
The WannaCrypt ransomware spread to devastating effect last week using worm -like capabilities
that relied on a recently patched vulnerability in Microsoft's SMB file-sharing services (MS17-010).
WannaCrypt used a purloined EternalBlue exploit originally developed by the US National Security
Agency before it was leaked by the Shadow Brokers last month.
WannaCrypt's victims included the National Health Service, Spain's Telefónica and numerous other
organisations across the world. A techie at Telefónica confirmed that the initial infection vector
was a
phishing email . The scale of the attack prompted Microsoft to take the highly unusual step of
releasing patches
for unsupported operating systems , including Windows XP. ®
Re: Inevitable
Don't blame the NSA - anyone could have discovered this issue and weaponized it. Certainly
the NSA should have reported it to Microsoft but they apparently didn't ... who knows.
The real issue here is that Microsoft stopped has patching XP and Vista systems in an attempt
to force users to upgrade -- that's where the real money is in these vulnerabilities. So who's
going to make out like a bandit from WannaCry et al? Expect Microsoft Win 10 share to increase
over the next few months - they are the real winners here.
Mage
Re: The real issue here is that Microsoft stopped has patching XP
Actually technically they haven't stopped. (Vista yes).
BUT THE PATCHING IS NEARLY IRRELEVANT!
Like most other spam borne "attacks" this would be totally mitigated by
1) User training and common sense.
2) Better configured systems.
XP use by NHS is a red herring.
Even if EVERYONE used Linux* and it was updated daily, it will NOT stop this until the USERs are
better trained and use email properly.
[*Because all the spam based attacks would be aimed at Linux]
Ken Hagan
Re: Inevitable
"Because the likes of the FSB & PLA must be too stupid to have also discovered these types
of vulnerabilities."
If they knew about them, they didn't do a very good job of protecting their own gear from them.
M.
Re: Inevitable
Your Comment: "Yes, the NSA is criminal for making these immoral and unlawful cyber weapons..."
Unlawful? By what law, specifically? (NOTE: Title 10 and Title 50 authorities directly - and
legally - trump certain US laws.) As an analogy - It's not "illegal" for a policeman to speed
to catch up to a criminal. It's not "illegal" for the NSA to create tools to compromise computers.
You can argue all day as to whether it is illegal to DEPLOY tools, once created, against CERTAIN
computers, but I don't think you have a leg to stand on calling the fact that NSA *creates* such
a tool - if they even did create one themselves - in any way an illegal act.
Michael Habel
Re: Inevitable
Implying that Windows 8, and Windows 10 are better than an unmaintained Windows XP SP3 Installation.
Which can still do it's job. Probably better than those other Two numbskull OSs. Assuming Microsoft
were kind enough to continue supporting it. But, alas that way only madness lay. As XP does not
contain Tracker's, and (Cr)App Stores to take your Moneyz.
DuncanLarge
Re: Inevitable
"Don't blame the NSA - anyone could have discovered this issue and weaponized it. Certainly
the NSA should have reported it to Microsoft but they apparently didn't ... who knows."
It's clear the NSA intended to not inform Microsoft at all as this was part or their arsenal,
a secret tool on their version of a Bat Belt. We must blame the NSA as they developed it, hoarded
it and then lost control of it when it got out. This should be an example of how such organisations
should not be using such methods.
The only way Microsoft knew about this and patched this was because the NSA lost control of
the code to ShadowBrokers who then reported it to Microsoft giving them enough time to roll out
a patch before a public release.
As you correctly say, anyone could have developed code that exploits the flaw. But who detected
that flaw first? So who should have the social responsibility to improve the "cyber" defense of
at least their own nation by disclosing such a flaw?
The NSA found it. Kept it secret, then lost the code due to real humans making mistakes or
breaking in who discover a pot of "hacker gold" runnable and mature from the fist double click.
For this very reason Apple, correctly, refused to create a version of iOS that could be installed
on an iphone to weaken the pin entry screen to allow the FBI entry. Apple knew they could not
simply trust that this hacked version of iOS could be kept under control.
inmypjs
Re: Inevitable
"blaming a commercial company for not patching a 13 year"
I think blaming and criticising a company that sold you buggy vulnerable crap and refuses to
fix bugs because someone else didn't find and advise them of them soon enough is entirely justified.
I have some compilers from a company with a policy that finding a bug in an obsolete unsupported
version of the compiler entitles you to a free upgrade to a current supported version. That would
be the policy of a decent company (which Microsoft clearly isn't). Of course Microsoft's current
supported version being a piece of shit that no one wants would stymie such a policy.
Wayland
Re: So you're blaming a commercial company for not patching a 13 year old OS?
In my experience with embedded systems there is nothing particularly fancy about the way the
PC talks to the special hardware. There is nothing that says it can't be upgraded to say 32 bit
Windows 7 or even rewritten for Linux. Much of the code is written in C or Delphi. It would take
a bit of work but not impossible.
The problem is that like Microsoft the manufacturers have moved on. They are playing with their
next big thing and have forgotten about that old stuff.
What is needed is a commitment from the manufacturers to either support the gear for 30 years
or share the code and the schematics. Obviously a consideration would be required from the buyer,
I don't see why they should do that for free.
The easiest thing would be to keep XP going and Microsoft will do that if you pay them. The
next thing would be to fit each XP system with a hardware firewall. Don't expect XP to protect
itself, put a packet sniffing firewall in between.
Dr Who
You could look at an event such as that of the last few days as the Internet's version of a wildfire.
In the short run some damage is done but in the long run the fire's job is to clear out dead wood
and enable the regrowth of a stronger, healthier ecosystem. Short term pain for long term gain.
Lost all faith...
And in a few years it will all be forgotten.
Nachi / Blaster anyone?
katrinab
Not really.
"We've installed the MS security patch, we've restored from back-up. Everything's OK now".
Papworth NHS Trust has had something like 16 of these ransomware attacks in the last 12 months,
and hasn't done anything. It is going to take a lot more than this to change management attitudes.
Mage
Internet's version of a wildfire.
No, because very few organisations and users will learn the real lessons.
Patching and AV inevitably often is bolting the stable door after horses gone for the first
hit. Yet proper user training and proper IT configuration mitigates against almost all zero day
exploits. I struggle to think of any since 1991.
Firewalls, routers, internal email servers (block anything doubtful), all superfluous services
and applications removed, no adhoc sharing. users not administrators, and PROPER training of users.
Anonymous Coward
I wish! The idiots who think it's fine to run XP are paid ten times more than me and they'll
still be in the same role this time next year. They'll be no getting rid of dead wood, just more
winging it and forcing underpaid Techies to work more weekends after more screw ups.
Stuart 22
Is it just me?
Its surely incredible that a lone pizza stuffed actor could get immediate access to the worm
and spend a night before he spotted the 'call home' vector? Is that really that hard? And beat
the best resourced detection agencies worldwide?
Surely every IT detective agency including GCHQ would have sandboxed it on first sight, thrown
their best at it if only to beat their friends across the pond, to save Jeremy Hunt & Mother Theresa's
bacon just ahead of a new funding opportunity (aka new government).
It all smells not only of pizza but planted news. And if it is genuine what on earth are we
paying this organisation and every anti-virus firm for?
Andy Non
Re: Experts all giving advice how how to stay secure
Went to the doctor's surgery this morning. All the computers were down. I queried if they'd
been hit with the malware, but apparently it was as a preventative measure as their main NHS trust
has been badly hit, so couldn't bring up any records or even know what the wife's blood test was
supposed to be for. Next I'm expecting the wife's hospital appt to be canceled due to the chaos
it is causing.
I wonder if we can get a go-fund-me page set up to hire someone to track down this hacker scum
and take out a hit on them? A bullet to the brain may give other scumbags something to think about.
Voyna i Mor
Re: Experts all giving advice how how to stay secure
The answer is not to avoid Windows. It's for our so-called security agencies to get to understand
that they are not supposed to be a dirty tricks department collecting weapons for use against
others, but that they are supposed to work on our national security - which includes public and
private services and businesses as well as the Civil Service.
The fact that May and Rudd seem totally unable to get what could go wrong post-Snowden suggests
that when one of them became PM, a school somewhere missed the bullet of a particularly anal retentive
geography teacher.
Anonymous Coward
Re: Experts all giving advice how how to stay secure
Actually Windows 10 was affected, but because it patches more aggressively the March fix was
already applied to must unless they had different WSUS settings in a business/edu environment.
Ferry Michael
Re: Experts all giving advice how how to stay secure
Windows 10 STILL has SMBv1 needlessly enabled by default. Should either be disabled by default
or removed all together. Wonder when someone will find another exploitable weakness. Staying secure
means turning off protocols you don't need.
I have a dual boot laptop that has not booted to Windows since before March - I need to review
what services it has enabled to make it a bit more secure before I connect it to the Internet
to download latest patches.
Patching and anti-virus software take time to apply after a vulnerability has been discovered.
That can be too late.
roblightbody
Re: Experts all giving advice how how to stay secure
From
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
"Customers running Windows 10 were not targeted by the attack today."
Voland's right hand
Re: Experts all giving advice how how to stay secure
Some people do not have any choice. When the X-ray machines in the affected hospital trusts
were bought using Windows XP (or even 2001) imaging software, that was state of the art. The issue
is that the life of a piece of equipment like this vastly exceeds the lifespan of the OS that
was used for the control system. On top of that, quite often these cannot be patched as the software
is written so badly that it will work only with a specific patch-level of the core OS.
That CAN and SHOULD be mitigated by:
0. Considering each and every one of those a Typhoid Mary in potentia
2. Preventing any communication except essential management and authentication/authorization
going out
3. Providing a single controlled channel to ship out results to a location which we CAN maintain
and keep up to date.
Instead of that, criminally stupid idots at NHS IT in the affected trusts as well as other
enterprises which were hit:
1. Put these unpatchable and unmaintainable machines in the same flat broadcast domain with
desktop equipment. There was no attempt at isolation and segmentation whatsoever.
2. In some cases allowed use of unrelated desktop applications (at ridiculously ancient patch-levels)
such as Outlook or even Outlook Express.
3. Opened file sharing on the machines in question.
Each of these should be a sackable offense for the IT staff in question.
mcpharm
Re: Experts all giving advice how how to stay secure
It's more than incompetent IT people and way worse and virtually impossible to fix.
There is a lot of niche or specialist custom software used in the nhs that can only work on
XP and ie 6 period. Most of the people who wrote are dead or retired etc
Systems vendors to the NHS are borderline criminal. In pharmacy, there are only 1 of 4 mandated
systems vendors you can choose. The 3 desktop based ones have so much legacy crap etc that they
still only work on windows 7. They also insist on bundling in a machine to just a stupid high
cost to a tech illiterate customer base - generally a cut down crappier version of something you
could by uin argos for 300 quid they will charge over a grand for. Their upgrade cycles are a
f**king joke and their business model makes their customers very reluctant to do so as they have
fork out silly money
for a new shit machine just cos their vendors tells they have to .. our superdupa crap shit
fuck software will only work on a machine we provide. Emis/proscript have alot to answer for ..
Lots of the staff and their employers are basically proud of being a digital numbskull. "I
am healthcare professional, why should i have to know anything about this" and the drones are
so poorly paid / bitched at incessantly about everything they just have an" i dunno i just work
here, that's not my job attitude" I have to screenshare to train people how to use our websites
.. this means i have to get them stick a url into their browser, that's it ... you have no idea
how many can't do that .. then get all offended when i ask them what browser they are using ..
"i don;t know, why should i know that, i just use google" is always the response .. when half
the nhs work force doesn't know what a f**king browser is and peversely proud of the fact they
can't type a url into a brower address bar, how on earth are we ever going to hav any sunnvbnf0ijgogjrnb;vzjnav;kjnnf;kqgfnjv;jnf;jjvn;w
Data Security has turned into one of these tick box things, everyone has dire warning, you
will be fined loads of money for doing something wrong that you don't understand and actively
don't want to understand so no one gives a f**k as long as they can say they ticked the right
boxes.
Anonymous Coward
A dish best served cold
Now, I would *hate* to start an internet rumour... but didn't the USA promise a retaliation?
:-)
- https://www.theguardian.com/us-news/2016/dec/16/obama-retaliation-russia-hacking-us-election
- http://www.bbc.com/news/world-39919249
Yupp, there was some collateral damage amongst their allies, but thats the new normal.
Anon because I might be right ;-)
Naselus
Re: A dish best served cold
"Anon because I might be right"
You aren't.
Firstly, a state actor attack would be far better targeted. Stuxnet, for example, actually
checked the serial numbers of the centrifuges it targeted to ensure that it only hit ones created
in the right date span to impact only those bought by Iran. The vector on this attack, on the
other hand, literally just spammed itself out to every available IP address that had port 445
open.
Second, US retaliation would almost certainly involve using a few zero-days. If you want to
prove that you have vastly more power than your opponent, then you want to do something that literally
resembles friggin' magic from his point of view. You want to show him that he can do nothing whatsoever
to defend his critical infrastructure from your attacks. This did not; nothing in this hadn't
already been discovered and patched. If the best thing the US can throw at Russia could be taken
out by just switching on your WSUS server in the past three months, then there's no point even
doing it because it would make them look weak, not strong.
Thirdly, and most importantly, most of the original bits of this were actually quite shittily
written. Oh sure, there was a genuine bit of high-tech NSA code in there from the shadow broker
leak... but there was also a fair load of primitive crap there too. It's a bit like an 16 year
old came into possession of an F-16; it was destructive as hell but he didn't really know how
to fly it.
I've just finished in a webinar on the incident, and there's literally 5 different layers of
my SMB's security that blocked this (patching, permissions, firewall, commercial AV, VLANs). And
we're not exactly cutting-edge - just running best practice.
In short, if this was state-backed, then the state in question would have to be somewhere like
Honduras, not one of the big-league infosec powers.
Anonymous Coward
On the topic of NSA exploits being used by WannaCry, was the DOUBLEPULSAR exploit patched with
MS17-010?
Commswonk
I can't help thinking that announcing the discovery of the kill switch might not have been
a good idea.
And you should see the number of downvotes I got in another thread for suggesting exactly that.
Another commentator stated (if I understood him correctly) that the "public announcement" was
more or less irrelevant because security experts' chatter on blogs would have given the game away
anyway.
In turn that made me think along the lines of " FFS what sort of security experts swap notes
on blogs that may be / almost certainly are open to being read by the hackers "
I think I despair... if the above is true then there is simply no hope.
Norman Nescio
Possibly not an intentional kill switch
As the Malwaretech blog entry here:
https://www.malwaretech.com/2017/05/how-to-accidentally-stop-a-global-cyber-attacks.html
points out, it was quite possibly not an intentional kill switch.
Some malware probes for the existence of a selection of randomly generated domains. Some sandbox
VMs respond to all DNS lookups by providing back the IP address of the sandbox VM instance. If
the malware sees a positive response to the DNS lookups (which should fail), then the logic is
that it is probably running in a sandbox VM, which may well be being used to analyse/investigate
the malware, so the malware stops running.
The single lookup of the unusual domain name was possibly a poor implementation of this technique.
Alternatively, it is an intentional kill switch, used during development, with a local DNS
server on the malware developer's LAN, the function of which was to prevent infection of other
devices on the same LAN. If anyone keeps records of DNS lookups, it might be interesting to see
where the first lookups came from.
Bill Gray
Re: Possibly not an intentional kill switch
@Norman Nescio : "...The single lookup of the unusual domain name was possibly a poor implementation
of this [sandbox detection] technique."
I read the Malwaretech log (excellent description of why you'd look for a nonexistent domain
to determine if you're sandboxed) and thought: OK, so the virus writer should check a randomly generated domain, instead of a fixed one. That
way, they can't all be registered, your virus can't be kill-switched the way this one was, and
your virus can still tell if it's being run in a sandbox.
Except the folks creating sandboxes might take the precaution of checking the domain. Instead
of returning a valid result for any garbage domain, check to see if it's been registered first.
Suddenly, the virus can no longer tell that it's running in a sandbox.
Except then, the virus author checks four or five valid domains; if they all return identical
results, you know you're running in a sandbox. (Reading further, I see that this method is actually
used in some cases.)
Except that _then_, the sandbox authors do some revisions so that seemingly accurate results
are returned that are actually remapped by the sandbox code.
This is all outside my area of expertise. Still, I could see a nearly endless cycle of fix/counter-fix
going on here.
Blotto
Ransome code is not proxy aware, kill switch won't work in most enterprises.
the code is not proxy aware and the kill switch would not work in well structured environments
where the only access to the net is via a configured non transparent proxy.
Enterprises will need to think a bit harder about how they ensure the kill switch is effective
this time. The miscreants wont make this same mistake next time.
Talking about the kill switch is good, wouldn't have taken the miscreants long to work out
something was not right anyway.
Anonymous Coward
What is the motivation here? Is all it seems to be...
<Black Helicopter Icon>
Ransomware usually works on a relatively widespread basis but usually SMB, and domestic users.
Big organisations and governments, generally are defended (although clearly some well publicised
exceptions)
The beneficiaries are usually relatively safe as law enforcement cannot usually be bothered
to investigate and the cash rolls in for the most desperate victims.
In this case, knowing there are a number of nation state backed cyber defence teams looking
into this... they either a) have balls big enough to need a wheelbarrow and believe that they
wont get caught no matter what and cyber defence is really too hard to deliver effectively, regardless
of backers. or b) that they are insanely stupid and greedy and are not following the news...
Or is this already a state backed exercise from somewhere and is simply a global experiment
at our expense? The fact the original flaw was used by the NSA is not really relevant, it simply
got it publicity but was clearly available for a long time.
Anonymous Coward
Re: What is the motivation here? Is all it seems to be...
Given that the only safe/undetected way of laundering the bitcoins will be to buy drugs
or guns or other such illegal goods on the darkweb and then turn that into cash by selling it
on then the perps are as you say both greedy and insanely (criminally) stupid. No doubt they'll
have their comeuppance shortly - without being "caught" by any nation state backed cyber
defense
team - probably up some dark alley being stiffed by gangbangers.
Probably just some kid :-(
gerritv
The warning was there in Sep 2016!!
We were told to stop using SMB v1 in Sep 2016. The only reason to keep it enabled is to use
it with XP!
https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/
IanMoore33
MS should hire the NSA hackers
maybe they can teach them something about software
Anonymous Coward
In light of this threat I just got around to patching a somewhat neglected Windows 7 PC. And
now it's got a message from Microsoft (falsely) saying it's not genuine. It may not be registered
but it's certainly a legitimately purchased copy. So far it's just a tiny message in the corner
of the screen but who knows what else it'll do. I don't have time for this. Guess I'll roll back
the update and take my chances.
This bullshit is what I blame more than anything, even the NSA, for outbreaks like this. If
Microsoft had an update channel for security patches only, not unwanted features and M$'s own
brand of malware, people would but alot more inclined to stay up to date.
Anonymous Coward
The goal here was 2 fold.
1. Hurt Russia.
2. Hurt NSA credibility.
Everything else is gravy for the attackers. Rumors running around that this is Deep State sponsored
coming out of various cliques in intelligence agencies in retaliation for the Vault 7 leaks.
Lion
Peer creds
The scum are obviously in hiding - either on a luxury yacht on the Black Sea or in a basement
somewhere. I'd hazard a guess it is the latter. There must be other scum in the same racket who
know who the are. I wonder if they have earned any street creds for what they did?
- - chaos (not really)
- - financial bonanza (nope)
- - media attention (big win)
- - shit disturbing (yep - mostly stirred the NSA and Microsoft)
- - rattle some chains (mostly IT departments)
- - peer envy (I doubt it)
Their reward beyond the $30K they collected will be prison (blackmail and extortion are felonies).
John Smith 19
So the haul from this little operation is currently what $60K?
V. Poor criminal work. Extortion technique needs more work. Clean up costs have probably been
in the $m.
Jim Birch
Re: So the haul from this little operation is currently what $60K?
This is a fairly typical ratio of realized proceeds of crime to cost of crime and prevention
measures. The economic case for crime reduction is overwhelming. But it's easier said than done.
People are creative, even (especially?) criminals.
truloxmyth
Its a sign of the times that no government is actually interested in Universal security, for the
greater good of human kind. We're at a point where everything is now based online, and everyone
in the world is connected.
The internet has removed the idea of 'borders' in the traditional sense!! I don't have to get
on a plane to Italy, to see Italy. I can log onto remote cameras and a host of other online services,
which mean I can be in the country without having to physically be in the country!
The NSA wasn't even bothered about protecting their own country... They didn't release this
data, to allow the problem to be solved. If I were American I would be Pissed that my own government
has been complicit in this entire debacle by keeping this quiet, and didn't release the information
to the wider security community when they found the holes!!
If your doctor found you had terminal cancer, but they had a product that would guaranteed
slowing of the cancer or entire removal of the disease then you would expect them to tell you
wouldn't you?! But when the shady NSA finds a potentially life threatening exploit, they keep
it to themselves?!... the middle letter of NSA stands for SECURITY for effs sake!!
There is no such thing as trust anymore between so called 'allies' as the NSA has just proved.
It has also proved that life is worthless to them. This is clearly due to their inability to see
the bigger picture of what they have A. Created, and B. Allowed to be released into the wild!!
Yes someone in their bedroom could have found the exploit, but that's a bedroom hacker/cracker.
But you put pretty much unlimited resources and man power behind a department, then they are clearly
going to come up with the exploit a billion times faster than a sole agent. Or even a collective
of agents separated over the globe.
So all this stupidity that the NSA shouldn't be held accountable should be rethought. Because
they CLEARLY are at fault here, for NOT DISCLOSING THE INFORMATION LAST YEAR!!!
Notable quotes:
"... At a minimum, Microsoft clearly should have provided the critical update in March to all its users, not just those paying extra. Indeed, " pay extra money to us or we will withhold critical security updates " can be seen as its own form of ransomware. ..."
"... This attack happened because the US Government didn't do it's job. It's primary task is national defense. It kept a vulnerability to itself to attack foreigners instead of protecting it's own infrastructure, businesses and individuals. The government had these tools taken and passed around for everyone to use. And crap like this is why governments can never be allowed to have backdoors. The secrets will always get out. Everyone is vulnerable. ..."
"... There are more than enough XP users in the world for Microsoft to dedicate resources and turn a profit supporting it. Arbitrary sunset dates disconnected from reality of who is still using software amount to nothing more than sales tools intended to extort upgrade revenue.... buy this or get owned. ..."
"... I personally don't believe vendors should be allowed to walk away from safety defects in products in order to make money on upgrades. Buffer overflows are entirely preventable classes of software failures. It is a tractable problem to solve. That it may not be in the case of XP isn't the end users problem. ..."
"... XP was far easier to lock down and fully secure than 8 or 10 with that bullshit telemetry, and it had far fewer hardware restrictions. It is smaller and faster and more capable at most of my tasks than most modern systems (example: I use ManyCam 3.0.80 - 2000/XP-Era multi-cam software. Runs like a champ on XP with 4 webcams, I go 7 [Ultimate] or higher, I can no longer use more than 2 webcams despite the software having the ability to access them and me having more than enough USB bandwidth for the uncompressed video streams.) ..."
"... Most real IT pros know that XP was far superior to the locked-down and (quite often) over-optimized (as in the optimizations go so far as to make the code more complex and actually runs slower due to shit like cache misses and what not) bullshit that is anything after Windows 7. ..."
"... Forever support isn't reasonable, but at the same time vendors using security update channels to push unwanted upgrades for the benefit of the vendor is equally bad. ..."
"... They already exist. They're called routers. Network routers can be configured to provide great deal of protection to machines that are older and cannot be patched. Many contain firewall software. Even simple ones can be configured to block traffic on vulnerable ports. ..."
"... Abandoning Operating Systems is a cruel trick played by vendors who want the new revenue from upgrades...no matter what the cost in lost-business, learning-curves, and incompatibilities with existing practices may be to the customers.. Spending money on maintaining the security (even excluding features) of superceded products distracts from development of improved products, and is not in the vendors' self-interest. ..."
"... do those devices NEED internet connection? serious question as i don't know. if not, no problem ..."
"... Bad car analogy. Firstly many old cars are banned from using critical infrastructure like highways (or in some cases any roads) for their obvious threat to third parties and their owners. ..."
In the
aftermath of ransomware spread
over the weekend, Zeynep Tufekci, an associate professor at the School of Information and
Library Science at the University of North Carolina, writes an opinion piece for The New York
Times:
At a minimum, Microsoft clearly should have provided the critical update in March to
all its users, not just those paying extra. Indeed, "pay
extra money to us or we will withhold critical security updates" can be seen as its own
form of ransomware.
In its defense, Microsoft probably could point out that its operating systems have
come a long way in security since Windows XP, and it has spent a lot of money updating old
software, even above industry norms.
However, industry norms are lousy to horrible, and it is reasonable to expect a company
with a dominant market position, that made so much money selling software that runs critical
infrastructure, to do more.
Microsoft supported Windows XP for over a decade before finally putting it to sleep.
In the wake of ransomware attacks, it stepped forward to release a patch --
a move that
has been lauded by columnists. That said, do you folks think it should continue to push
security updates to older operating systems as well?
acoustix ( 123925 ) on Monday May 15, 2017 @01:01PM (#54419597)
Wrong Approach (Score:2)
This attack happened because the US Government didn't do it's job. It's primary task is
national defense. It kept a vulnerability to itself to attack foreigners instead of protecting
it's own infrastructure, businesses and individuals. The government had these tools taken and
passed around for everyone to use. And crap like this is why governments can never be allowed
to have backdoors. The secrets will always get out. Everyone is vulnerable.
WaffleMonster ( 969671 ) on Monday May 15, 2017 @12:09PM (#54419177)
Artificial scarcity (Score:2)
There are more than enough XP users in the world for Microsoft to dedicate resources
and turn a profit supporting it. Arbitrary sunset dates disconnected from reality of who is
still using software amount to nothing more than sales tools intended to extort upgrade
revenue.... buy this or get owned.
I personally don't believe vendors should be allowed to walk away from safety defects
in products in order to make money on upgrades. Buffer overflows are entirely preventable
classes of software failures. It is a tractable problem to solve. That it may not be in the
case of XP isn't the end users problem.
jrifkin ( 100192 ) on Monday May 15, 2017 @11:55AM (#54419015)
Yes. It's like vaccinations (Score:2)
If the number of older systems is large enough, then Yes, Microsoft should release patches
for them.
They should do this for two reasons:
1) Reducing the number of infected systems helps protect others from infections
2) It protects the innocent, like those whose Medical Care was interrupted in the UK, from
collateral damage.
Who pays for it? Microsoft. They have benefited from the sale of all those systems, and
certainly have enough cash to divert some to supported old but prevalent systems. Also, the
fact that people still use MS systems, even if they're old, benefits MS in some way by helping
them maintain market share (and "mindshare"). Odds are that these systems will eventually be
replaced by more MS systems, representing future revenue for MS.
Khyber ( 864651 ) <[email protected]> on Monday May 15, 2017 @11:50AM (#54418981) Homepage
Journal
Re: Silly idea (Score:2)
"I think there is clearly one party at fault, and it is IT."
Why so? XP was far easier to lock down and fully secure than 8 or 10 with that bullshit
telemetry, and it had far fewer hardware restrictions. It is smaller and faster and more
capable at most of my tasks than most modern systems (example: I use ManyCam 3.0.80 -
2000/XP-Era multi-cam software. Runs like a champ on XP with 4 webcams, I go 7 [Ultimate] or
higher, I can no longer use more than 2 webcams despite the software having the ability to
access them and me having more than enough USB bandwidth for the uncompressed video streams.)
Most real IT pros know that XP was far superior to the locked-down and (quite often)
over-optimized (as in the optimizations go so far as to make the code more complex and
actually runs slower due to shit like cache misses and what not) bullshit that is anything
after Windows 7.
swb ( 14022 ) on Monday May 15, 2017 @12:20PM (#54419293)
It's an existential problem (Score:2)
Forever support isn't reasonable, but at the same time vendors using security update
channels to push unwanted upgrades for the benefit of the vendor is equally bad.
My guess is that we're going to be getting to the end of the road of the "nasty, brutish
and short" state of nature in the software industry and start seeing more regulations.
Vendors will be able to EOL their products, but will also have to supply security updates
for N years after the product is officially ended. Vendors will be required to maintain a
security update channel which may not be used for pushing upgrades or unrequested new
products.
An interesting solution would be to let vendors "expire" a version by inserting a patch
that boots the OS at a warning page requiring a firm verbal commitment ("I agree this is
obsolete") before booting any further. Vendors would be REQUIRED to do this for operating
systems they had obsoleted but only after their N years of post-EOL support had ended.
This way, nobody escapes the product being EOL. Customers can still use it, but must
affirmatively acknowledge it is obsolete. Vendors are required to keep supporting it for a
really long time after official EOL, but they can kill it more completely but only after the
EOL support period.
Anonymous Coward on Monday May 15, 2017 @10:44AM (#54418429)
No (Score:5, Insightful)
No. You can't support legacy software forever. If your customers choose to stay with it
past it's notified EOL then they are SOL. Any company using XP that got hit by this can only
blame themselves.
jellomizer ( 103300 ) on Monday May 15, 2017 @10:48AM (#54418451)
Re:No (Score:4, Insightful)
I will need to agree with conditions. If the Tech company is selling service contracts for
that product, they will need to update it. However like XP and older, where the company isn't
selling support, and had let everyone know that it off service, they shouldn't need to keep it
updated. Otherwise I am still waiting for my MS DOS 6 patch as it is still vulnerable to the
stoner virus.
AmiMoJo ( 196126 ) <mojo AT world3 DOT net> on Monday May 15, 2017 @12:11PM (#54419217)
Homepage Journal
Re:No (Score:4, Insightful)
The people providing support should be the ones making MRI scanners, ATMs and other expensive
equipment that only works with XP. Even when XP was brand new, did they really expect those
machines to only have a lifetime of around 10 years? Microsoft was clear about how long
support was going to be provided for.
It seems that people are only just waking up to the fact that these machines have software and
it needs on-going maintenance. The next decade or two will be littered with software bricked
but mechanically sound hardware, everything from IoT lightbulbs to multi-million Euro medical
equipment.
In fact it's already happening. You can buy DNA sequencers on eBay, less than a decade old and
original price $500,000, now barely worth the shipping because the manufacturer abandoned
support.
number6x ( 626555 ) on Monday May 15, 2017 @12:18PM (#54419269)
They already exist (Score:4, Insightful)
They already exist. They're called routers. Network routers can be configured to
provide great deal of protection to machines that are older and cannot be patched. Many
contain firewall software. Even simple ones can be configured to block traffic on vulnerable
ports.
In this case, a router could be configured to keep the SMB port (445) blocked. A router,
with updated software, and a firewall gateway can help protect even older devices with
embedded code that may no longer be supported.
Of course, it goes to say, that you must keep the router's software updated and not use
default credentials on the router.
The NHS decided to not upgrade many old systems because the threat was deemed minimal.
Offices were urged to upgrade but funds were not made available and infrastructure budgets
were cut again and again. Multiple bad decisions led to this result.
Many things could have prevented it. Better funding, better threat assessment, the NSA
informing Microsoft of the vulnerability so it could have been patched years ago, and on and
on...
In the end we are here, and hopefully threats will be re-prioritized and better protections
will be put in place in the future (I could not keep a straight face while typing that and
finally burst out laughing).
bugs2squash ( 1132591 ) on Monday May 15, 2017 @10:45AM (#54418433)
Don't be silly (Score:2)
this did not need to be fixed with an OS patch, it could have been prevented with better
network security policies. I would be surprised if someone hadn't said something about
addressing the vulnerability earlier but probably got ignored because of some budgetary issue.
It would be more reasonable to call for continued money to be made available to address
these vulnerabilities after a system has gone into production and a move to use more open
source solutions where users can share patches.
CAOgdin ( 984672 ) on Monday May 15, 2017 @11:07AM (#54418613)
I recommend a Subscription model... (Score:3)
Abandoning Operating Systems is a cruel trick played by vendors who want the new revenue
from upgrades...no matter what the cost in lost-business, learning-curves, and
incompatibilities with existing practices may be to the customers.. Spending money on
maintaining the security (even excluding features) of superceded products distracts from
development of improved products, and is not in the vendors' self-interest.
Given that a new Operating system (retail) is in the $100-$150 range, I'd propose "Life
Extension" service subscription, solely for security updates in the $30-35/year range...with a
required minimum of 10,000 customers to keep maintaining the service. That provides enough
revenue ($1,000,000+ per annum) to support a small, dedicated staff.
Frankly, there's no reason that a M$ couldn't engage in a Joint Venture with a small
qualified, independent security firm to provide the service, with special access to
proprietary information within the O.S. vendor.
It would be an investment in the rehabilitation of the O.S. vendors' reputation, because M$
has gotten quite high-handed in recent years, dictating (or even forcing) software on
unwilling customers.who have existing businesses to run.
ToTheStars ( 4807725 ) on Monday May 15, 2017 @11:29AM (#54418801)
What if we tied support to copyright? (Score:5, Interesting)
Slashdot generally doesn't like ludicrously-long copyright terms, right? What if we made
maintenance a requirement for retaining copyright over software? If Microsoft (or whoever)
wants to retain a copyright on their software for 70 years, then they'd better be prepared to
commit to 70 years of support. If they want to EOL it after 5 years or 20 years or whatever,
and wash their hands of responsibility, that's fine, but then it's public domain. Why should
we let companies benefit from software they don't support anymore?
This could also work for art works, as well -- because copyright exists "To promote the
Progress of Science and useful Arts," we could make it a requirement that an author (or
company, or whatever) needs to be distributing (or licensing for distribution) a work to have
copyright on it. When it's out of print, it enters the public domain.
Hartree ( 191324 ) on Monday May 15, 2017 @11:07AM (#54418625)
Yes, because WinXP was never killed off. (Score:2)
It also lives on in many scientific instruments. An old mass spec that runs XP (or even
older. I regularly maintain X Ray diffraction machines that still run DOS) usually can still
do the day to day job just fine. The software usually hasn't been supported for many years and
won't run on anything newer. But replacing the instrument could cost a large amount of money
(250K or up in many cases).
Research budgets aren't growing and I work for a university in a state that can't pass a
budget. We just don't have the money to throw out older systems that work well just because
the software is outdated. We just take them off the network and use other means to get the
data transferred off of them.
ganjadude ( 952775 ) on Monday May 15, 2017 @11:37AM (#54418873) Homepage
Yes, because WinXP was never killed off. (Score:2)
do those devices NEED internet connection? serious question as i don't know. if not, no
problems
DontBeAMoran ( 4843879 ) on Monday May 15, 2017 @11:22AM (#54418727)
Re:Bitcoin is the problem (Score:2)
Because ransomware did not exist before Bitcoin. :rolleyes:
jellomizer ( 103300 ) on Monday May 15, 2017 @11:12AM (#54418661)
Re:Silly idea (Score:2)
What happens if a still used software isn't owned by anyone any more. The Company is out of
business, There is no source code available. There is a point where the end user has some
responsibility to update their system. Like the Model-T they may still keep it, and use it for
a hobby, but knowing full well if you take it on the Highway and get in an accident you are
probably going to get killed.
thegarbz ( 1787294 ) on Monday May 15, 2017 @12:08PM (#54419169)
Re:Silly idea (Score:3)
Bad car analogy. Firstly many old cars are banned from using critical infrastructure
like highways (or in some cases any roads) for their obvious threat to third parties and their
owners.
Also this isn't hobbies we're talking about. No one gives a crap if someone's Model T toy
breaks down, just like no one will cry about the Windows XP virtual machine I play with at
home.
The only complaints are against critical services, internet connected machines that operate
and provide livelihoods for the owners. If the software isn't owned by anyone, ... well I'm
sure the owner provided an unbiased risk assessment as to whether they should migrate to
something that is supported by someone right? Didn't think so.
The end user has 100% of the responsibility, and dollars don't change that.
WannaCry offers free decryption for some random number of files in the folder C:\Intel\<random
folder name>\f.wnry. We have seen 10 files decrypted for free.
In the first step, the malware checks the header of each encrypted file. Once successful, it calls
the decryption routine, and decrypts all the files listed in C:\Intel\<random folder name>\ f.wnry.
A code snippet of the header check:

The format of the encrypted file:

To decrypt all the files on an infected machine we need the file 00000000.dky, which contains
the decryption keys. The decryption routine for the key and original file follows:

Bitcoin activity
WannaCry uses three Bitcoin wallets to receive payments from its victims. Looking at the payment
activity for these wallets gives us an idea of how much money the attackers have made.
The current statistics as of May 13 show that not many people have paid to recover their files:
- Wallet 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
-

- Wallet 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
-

- Wallet 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
-

The attackers appear to have earned a little over BTC 15.44 (US$27,724.22). That is not much considering
the number of infected machines, but these numbers are increasing and might become much higher in
the next few days. It's possible that the sink holing of two sites may have helped slow things down:
- hxxp://www[dot]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[dot]com
- hxxp://www[dot]ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[dot]com
Multiple organizations across more than 90 countries have been impacted, according to reports.
We will update this blog as we learn more.
"Cyber criminals may believe they are anonymous but we will use all the tools at our disposal
to bring them to justice," said Oliver Gower from the National Crime Agency.
A computer security expert
credited with stopping the spread of the ransomware on Saturday by activating a digital "kill
switch" warned on Sunday that a fresh attack was likely.
The expert, known only as MalwareTech on Twitter, said hackers could upgrade the virus. "Version
1 of WannaCrypt was stoppable but version 2.0 will likely remove the flaw,"
he said on
Twitter . "You're only safe if you patch ASAP."
On Sunday, Microsoft issued a security bulletin marked "critical" including security updates that
it said "resolves vulnerabilities in Microsoft Windows".
It emerged over the weekend that NHS Digital last month emailed 10,000 individuals in NHS organisations
warning them to protect themselves against the specific threat of ransomware and included a software
patch to block such hacks on the majority of systems. However, it would not work with outdated Windows
XP systems that still run on about 5% of NHS devices.
NHS Digital said it did not yet know how many organisations installed the update and this would
be revealed in a later analysis of the incident.
... ... ...
Amber Rudd, the home secretary, who is leading the response to the attack, said the same day:
"I don't think it's to do with ... preparedness. There's always more we can all do to make sure we're
secure against viruses, but I think there have already been good preparations in place by the NHS
to make sure they were ready for this sort of attack."
In a blog post late Sunday, Microsoft President Brad Smith appeared to tacitly acknowledge
what researchers had already widely concluded: The ransomware attack leveraged a hacking tool,
built by the US National Security Agency, that leaked online in April.
He also poured fuel on a long-running debate over how government intelligence services should
balance their desire to keep software flaws secret – in order to conduct espionage and cyber
warfare – against sharing those flaws with technology companies to better secure the internet.
"This attack provides yet another example of why the stockpiling of vulnerabilities by
governments is such a problem," Smith wrote. He added that governments around the world should
"treat this attack as a wake-up call" and "consider the damage to civilians that comes from
hoarding these vulnerabilities and the use of these exploits."
The NSA and White House did not immediately respond to requests for comment about the Microsoft
statement.
A general view of the Dharmais hospital in Jakarta, Indonesia May 14, 2017. REUTERS/Darren
Whiteside
The Dharmais hospital in Jakarta was targeted by the Wannacry "ransomware" worm. Photo:
Reuters/Darren Whiteside
US President Donald Trump on Friday night ordered his homeland security adviser, Tom Bossert, to
convene an "emergency meeting" to assess the threat posed by the global attack, a senior
administration official told Reuters.
Senior US security officials held another meeting in the White House Situation Room on Saturday,
and the FBI and the National Security Agency were working to help mitigate damage and identify
the perpetrators of the massive cyber attack, said the official, who spoke on condition of
anonymity to discuss internal deliberations.
The investigations into the attack were in the early stages, however, and attribution for
cyberattacks is notoriously difficult.
The original attack lost momentum late on Friday after a security researcher took control of a
server connected to the outbreak, which crippled a feature that caused the malware to rapidly
spread across infected networks.
Infected computers appear to largely be out-of-date devices that organizations deemed not worth
the price of upgrading or, in some cases, machines involved in manufacturing or hospital
functions that proved too difficult to patch without possibly disrupting crucial operations,
security experts said.
Microsoft released patches last month and on Friday to fix a vulnerability that allowed the worm
to spread across networks, a rare and powerful feature that caused infections to surge on Friday.
Code for exploiting that bug, which is known as "Eternal Blue," was released on the internet last
month by a hacking group known as the Shadow Brokers.
The head of the European Union police agency said on Sunday the cyber assault hit 200,000 victims
in at least 150 countries and that number would grow when people return to work on Monday.
Notable quotes:
"... French police said there were "more than 75,000 victims" around the globe, but cautioned that the number could increase "significantly". ..."
International investigators hunted for those behind an unprecedented cyber-attack that
affected systems in dozens of countries, including at banks, hospitals and government agencies, as
security experts sought to contain the fallout.
The assault, which began on Friday and was being described as the biggest-ever cyber ransom attack,
struck state agencies and major companies around the world - from Russian banks and British hospitals
to FedEx and European car factories.
"The recent attack is at an unprecedented level and will require a complex international investigation
to identify the culprits," said Europol, Europe's police agency. Europol said a special task force at its European Cybercrime Centre was "specially designed to
assist in such investigations and will play an important role in supporting the investigation".
The attacks used ransomware that apparently exploited a security flaw in Microsoft operating systems,
locking users' files unless they pay the attackers a designated sum in the virtual currency Bitcoin. Images appeared on victims' screens demanding payment of $300 in Bitcoin, saying: "Ooops, your
files have been encrypted!" Payment is demanded within three days or the price is doubled, and if none is received within
seven days the files will be deleted, according to the screen message.
But experts and government alike warn against ceding to the hackers' demands. "Paying the ransom does not guarantee the encrypted files will be released," the US Department
of Homeland Security's computer emergency response team said.
Mikko Hypponen, chief research officer at the Helsinki- based cyber security company F-Secure,
told AFP it was the biggest ransomware outbreak in history, saying that 130,000 systems in more than
100 countries had been affected.
... .... ....
French police said there were "more than 75,000 victims" around the globe, but cautioned that the number could increase "significantly".
on May 12, called "encryption" (Wannacry) "worm" blackmail software in large-scale spread around
the world.The software using the Windows SMB services vulnerabilities, documents, pictures, etc.
Of computer implementation of high-strength encryption, and ransom.Currently, including universities,
energy and other important information system, more class user attack, have serious security threat
to China's Internet network.
a, infected host emergency isolation methods given WannaCry worm has
a great risk, all the known infected host must isolate their work from the current network.
in view of the file has been damaged by worms, as of 2017/5/14 haven't found any effective means
to restore.To prevent further spread worms, it is forbidden to infected host any file copy to other
host or device, it is strictly forbidden to known infected host to access any network.
2, important documents emergency handling methods in order to ensure the important document is
not destroyed by WannaCry worms, minimize loss, all uninfected hosts or ban on uncertain whether
infected host.
the type host need to adopt the method of physical copy for processing, i.e., the host opens by
the professionals, remove all the hard disk where important files, and use the external devices mounted
to determine uninfected hosts will be copied.
to prevent secondary infection, copy the file must be in the isolation zone for processing.
it is strictly forbidden to hard disk may be infected by the IDE and SATA motherboard interface
mounted directly to the copy machine, in order to prevent the copying machine use the hard disk boot,
leading to possible infection.
existing in the network, have access to all Windows host should adopt the method of important
file backup.
after the physical copy process, in accordance with the: three, host, emergency detection strategy
is used to detect the emergency treatment.
the temporary absence of these conditions or because of some must be switched on, it is important
to ensure keep access to the Internet boot in out of the office network environment (such as 4 g
networks, ordinary broadband, etc.), at the same time must be the entire keep clear of the Internet.(access
to the Internet standard for success: can open the following web site in the browser, and see the
content as shown: www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
)
for classified machine cannot access to the Internet, make sure the web server, network configuration
and the domain name resolution to access the Intranet server.
the Intranet server home page must return the following contents:
sinkhole. Tech - where the bots party hard and the researchers harder. & lt;!- h4 - & gt;At the
end of the temporary boot process, shutdown and physical copy process.
3, host, emergency detection strategies in view of the physical copy after the host, to make the
following treatment:
test be mounted hard drive Windows directory, see if there are files: mssecsvc. Exe, if there
are infected.
in view of the host other boot, check whether there is a file system disk Windows directory: mssecsvc.
Exe.Check whether there is a service in the system mssecsvc2.0 (see specific operation at the end
of this section).Any one is exists to prove that is infected.
for there is a firewall with other logging equipment in the network, check whether there is in
the log of domain name: www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, if any, prove the existence
of network within the infected host.In view of the infected host detect, be sure to at the end of
the physical copy process format for all the hard disk.
similar to the host if there is a backup before 2017/4/13, full recovery operations can be performed
(including system disk as well as other all), a backup after this time may have been infected, not
for recovery.
in view of the network known to exist the infected host, prohibit open closed host, at the same
time to physical copies of the host process.For the host has been switched on, immediately shut down,
and the physical copy process.Attachment: the method of inspection service:
Windows + R key to open the "run" window:
input services. MSC enter, open the service administration page:
check all items in the" name "column, there mssecsvc2.0 suggests that infected.
4, uninfected hosts emergency defense strategy
to an infected host, there are four emergency defense strategy.
one strategy as the most effective means of defense, but takes longer.Other strategies for temporary
solution for unable to implement strategies for temporary use.
application strategy two or three in the host will not be able to access the network sharing,
please carefully use.
in no immediate application strategy and suggestion first application strategy four temporary
defence.No matter use what kind of temporary strategy, all must be application strategy as soon as
possible in order to achieve complete defense.
under 10 version for Windows host, suggest to upgrade to Windows 10 and update to the latest version
of the system.Because of the situation cannot upgrade, be sure to use an emergency defense strategy
for defense.
strategy one: install MS17-010 system patches
according to the system version, install patches MS17-010.With Windows 7 and above can be gained
through the automatic updates to install all patches, Windows xp, Windows 2003 and Windows vista
can be gained by installing temporary tools provided with the document.
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
strategy 2: closing loopholes related services
by professionals using the following command to close loopholes related services:
sc stop LmHosts
sc stop lanmanworkstation
sc stop LanmanServer
sc config LmHosts start = DISABLED
sc config lanmanworkstation start = DISABLED
sc config LanmanServer start = DISABLE
strategy 3: configure the firewall ban vulnerabilities related port
for Windows 2003 or Windows xp system, click on the start menu, and open the "control panel".
double click the" Windows firewall "option in control panel, click on the" exception "TAB,
and uncheck the" file and printer sharing ", and click ok.
for Windows 7 and above system, click on the start menu, open the control panel, click on the"
system and security "" Windows firewall".
in Windows firewall configuration page, click the" allow the procedure or function through
Windows firewall "option, click at the top of the" change Settings ":
in the list to find" file and printer sharing "checkbox, uncheck the, click ok in the end.
strategy 4: use the vulnerability defense tool
360 company provides tools for temporary immune defense worm, this tool can be downloaded in the
360 site.
directly to perform this tool can be simple to defence, every time to restart the host must perform
this tool again.
5, emergency public server and network security defense strategy
on public server (such as web sites, public system, etc.) most can connect to the Internet, for
Windows server 2008 r2 and higher versions, suggested that open system "automatically update" function,
and install all patches.
for Windows server 2003, you can choose four, uninfected hosts emergency strategy of defense strategy
for defense, at the same time Suggestions as soon as possible to upgrade to higher version of the
server (such as Windows 2008 r2).
according to the internal network, need to ensure the safety of the host of the case to prevent
possible infection.
without using the sharing function, but on firewalls, routers and other equipment 445 port access
is prohibited.
since this worm using domain name: www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com as "switch",
instantly attacks when unable to access the domain name.Therefore, the ban on the network security
devices such as firewall and IPS intercept this domain name, otherwise it will trigger the infected
host encryption process, cause irreparable damage.
use Intranet private DNS, be sure to configure the domain analysis, and point to survive in the
Intranet web server.The Intranet server home page should be returned the following contents:
sinkhole. Tech - where the bots party hard and the researchers harder.
& lt;!- h4 - & gt;
net letter tianjin municipal party committee office, network security and information technology
evaluation center
Date:2017-05-14
Tag:
do
emergency
Tianjin
global
worm
infection
WannaCry
method
virus
computer
Targets both large and small have been hit.
Renault said on Saturday it had halted
manufacturing at plants in Sandouville, France, and Romania to prevent the spread of
ransomware in its systems.
Among the other victims is a Nissan manufacturing plant in Sunderland, northeast
England, hundreds of hospitals and clinics in the British National Health Service,
German rail operator Deutsche Bahn and International shipper FedEx Corp
A Jakarta hospital said on Sunday that the cyber attack had infected 400 computers,
disrupting the registration of patients and finding records. The hospital said it
expected big queues on Monday when about 500 people were due to register.
'Ransom' paymentsmay rise
Account addresses hard-coded into the malicious WannaCry software code appear to show
the attackers had received just under US$32,500 in anonymous bitcoin currency as of 1100
GMT on Sunday, but that amount could rise as more victims rush to pay ransoms of US$300
or more to regain access to their computers, just one day before the threatened deadline
expires.
"I can confirm we've had versions without the kill switch domain connect since yesterday,"
Costin Raiu, director of global research and analysis team at Kaspersky Lab told Motherboard on
Saturday.
TiggertheMad ( 556308 )
writes: on Friday May
12, 2017 @07:19PM (
#54408293
) Homepage
Journal
National
Insecurity Agency (
Score: 4 , Informative) ]
The NSA (and other ABC agencies that are undoubtedly running the same game plan) are doing
what they are tasked with, finding ways to protect America and America's interests. Using hacking
as a tool to this end is (relatively) new in the old game of spycraft, so there are going to be
a few epic disasters like this before the black ops people start to figure out all the types of
blow back they can experience.
The US was really big on foreign covert action in the 50's, and it took the bay of pigs to
make people realize that there were ways that things could go horribly wrong. That didn't stop
covert action from being used, but I think it was employed more carefully afterwards. Having all
their shiny hacking toys stolen and having this happen is the hacking version of the 'Bay of Pigs'.
Also, while the NSA seems to have compiled a formidable array of exploits and tools to compromise
enemy systems, that doesn't mean that everyone else isn't playing the exact same game. The only
difference between the NSA and EVERY other state intelligence agency on the planet is that they
seem to be able to properly secure their black ops toys. Being one of the largest agencies of
this sort, there are going to be a lot of people in the know. And the more people involved, the
harder it is to keep a secret.
Mind you, that doesn't make this any less tragic or regrettable.
I sort of hope the CIA decides that it is in the US interest to find and vanish anyone connected
with this ransomware to make an example of them. Alas, that sort of thing only happens in implausible
Hollywood scripts.
ancientt ( 569920 )
writes: <
[email protected] > on Friday May 12, 2017 @08:07PM (
#54408453
) Homepage
Journal
Re:National
Insecurity Agency (
Score: 3 )
Remotely exploitable network vulnerabilities shouldn't happen, but there seems no practical
hope that they'll stop anytime soon. It would be negligent of legitimate spy agencies to fail
to search for them and arguably be able to take advantage of them. Imagine you're trying to find
out when an ISIS group is planning a bombing and you discover they're running a messageboard on
a Windows machine with an SMB exploit, do you tell Microsoft to patch the exploit?
You never know which of the vulnerabilities you'll be able to use, but if you dedicate sufficient
resources to finding them and building exploits for them, then there is a good chance you'll be
able to spy on whichever bad guy your agency needs to spy on when the need arises. Getting all
the vendors to patch the exploits you find does limit your own agency's ability to spy but you
have to assume it doesn't impair your enemies as significantly since the enemy doubtless will
have exploits you don't have.
What's the best solution? I suspect the best thing to do is build force-patch worms for every
exploit. If you write an exploit, you should also dedicate resources to the task of writing a
version of the exploit which pressures the owner of the exploited system to fix the problem. So
in this instance, as soon as the attacks started being seen in the wild, the NSA servers should
have launched a MASSIVE attack against any and all systems with the vulnerability which would
disable the vulnerable systems in the least painful ways along with alerting the owners of the
need to update their systems. Instead of getting "your files are encrypted and give hackers bitcoin
to recover" messages, the people with exploitable systems should be seeing warnings like "Your
system has been temporarily patched by the NSA for your own protection, please secure or update
your device to protect it from malicious actors."
The
Hajime botnet [arstechnica.com] may actually already be just the thing I'm describing. I'd
prefer to see the NSA take public responsibility, and I'm doubtful the NSA is actually responsible
for that one, but it is an example of how it could be done.
If I have a vulnerable system, I'd much prefer to see it hacked by the NSA instead of some
ransomware writer. Do I wish it wasn't hackable? Of course, but I accept that anything plugged
into a network might be hackable. I do what I can to protect it from everyone, including the NSA.
It's not that I'm worried about the NSA (because they have the resources to gain physical access
if they really want it) but if I do my best to build secure systems, then it's less likely I'll
wake up to a ransomware message some morning
mcswell ( 1102107 )
writes: on Friday May 12,
2017 @11:09PM (
#54409045
)
Re:Say
"thanks" to your "security"-agency... (
Score: 2 )
And why do you think Microsoft was able to patch this *before* the exploit was leaked by Shadow
Brokers?
Anonymous Coward writes: on Friday May 12, 2017 @08:56PM (
#54408607
)
Re:Say
"thanks" to your "security"-agency... (
Score: 1 )
microsoft is partly guilty in this for sure because A LOT of people have the updates turned
off since the windows 10 debacle, the lies, the telemetry, the diagtrack process, the broken windows
update service that sits iddle consuming 25% of your cpu, etc
but even a monkey like me that hears about the smb vuln, even if i dont know what it means
exactly because im just a user and not an engineer, i could tell it was BAD, so i patched the
living shit out of my computer
sorry but if youve had experiences with blaster, conficker, etc, you should know about this
kind of things already, again, not an engineer at all, but just hearing about it, looking the
ports affected this thing looked really bad
Man On Pink Corner
( 1089867 ) writes: on Friday
May 12, 2017 @08:29PM (
#54408529
)
Re:That
only happened to idiots. (
Score: 3 )
Microsoft told lie after lie after lie about their intentions. There was absolutely no reason
to believe that setting your update threshold to "Critical Only" would save you from an unsolicited
Windows 10 installation.
The only rational course of action for those who didn't want Windows 10 was to turn off Windows
Update entirely. Deny this all you want, but be prepared for justified accusations of victim-blaming.
Anonymous Coward , Friday May 12, 2017 @06:55PM (
#54408177
)
It hit
the NHS hard (
Score: 5 , Interesting)
I'm a doctor in the NHS. It hit my hospital hard. The bosses triggered the MAJAX protocols
meaning everyone off work was called to come in and help. Computers are used for everything, so
blood tests, admissions, scan requests, referrals, all had to be done by hand. The public were
asked to keep away from A+E because hundreds of people were waiting. It was terrifying how little
failsafe infrastructure there was. The hospital just stopped working.
TroII ( 4484479 )
writes: on Friday May 12, 2017
@08:28PM (
#54408521
)
Re:It
hit the NHS hard (
Score: 5 , Insightful)
And you use unpatched computers in a hospital WHY?
Because patches are often broken . Imagine these hospitals had applied the patch when Microsoft
released it, but the patch was faulty in some way, and all of the hospital computers went down
as a result. Instead of complaining the hospitals were running unpatched, you and/or many people
like you would be bitching and moaning that they were negligent to install the patch too soon.
Updates from Microsoft frequently include at least one broken patch. There was one update last
year that broke millions of peoples' webcams. There have been several updates that interfered
with settings and reverted them back to default configurations, and several more updates that
seemingly deleted group policy objects that had been configured by the domain administrator. There
was a patch around the new year that inadvertently disabled the DHCP service, despite the update
itself having nothing to do with DHCP. (Things that make you go hmmm.) This particular fuck-up
rendered a lot of machines not only broken, but totally irreparable without manual human intervention,
i.e. dispatching someone clueful to each of your premises to clean up the mess.
Patch deployment in any enterprise environment requires extensive testing. You have to coordinate
with your software vendors to make sure their applications are compatible with the update. If
you install Patch XYZ without first getting approval from Vendor123, you wind up invalidating
your support contracts with them. All of this takes time. In 2016, there were several months
in a row where Microsoft had to un-issue, repair, supersede, and re-release a broken patch
they'd pushed out. Put yourself in the shoes of an admin team who got burned by Windows Update
breaking your systems, especially repeatedly. Are you going to be in any hurry to patch? If you
were bitten by the DHCP bug, do you trust that the "critical SMB patch" really only touches SMBv1,
and isn't going to inexplicably corrupt Office or remove IPV4 connectivity on every computer it
touches?
If the PC your kid plays Minecraft on gets hosed by a broken patch, it's not that big of a
deal. The business world is a different story.
guruevi ( 827432 )
writes: <
evi@evcir[ ]ts.com ['cui' in gap] > on
Friday May 12, 2017 @07:03PM (
#54408215
) Homepage
What boggles
my mind (
Score: 4 , Informative)
Is that there are still 45k Windows machine that are directly connected to the Internet.
Any Windows machine I manage (mostly very specific medical software and medical machines) are
either VM (and thus behind a firewall and any service proxied to a BSD or Linux host) or airgapped.
cpm99352
( 939350 ) , Saturday May 13, 2017
@12:52AM (
#54409331
)
Plenty
of blame to spread around (
Score: 2 )
1, Microsoft has always had a disclosure that their OS is not suitable for life-critical applications
2. NSA has a dual mission -- the second (neglected) mission is to ensure the security of domestic
computer networks
Officials have claimed in the wake of the global ransomware attack that patient care has been
unaffected despite 45 NHS sites
being hit.
But hospitals across England and Scotland were forced to cancel routine procedures and divert
emergency cases in the wake of the attack, which has shut down access to computers in almost 100
countries. Here, patients and NHS workers reveal how the crisis has affected them.
Bill, a doctor at a hospital in London
I have been unable to look after patients properly. However much they pretend patient safety is
unaffected, it's not true. At my hospital we are literally unable to do any X-rays, which are
an essential component of emergency medicine. I had a patient this evening who we could not do
an X-ray for, who absolutely should have had one. He is OK but that is just one example.
My hospital is good in many ways but the IT system is appalling. I was shocked when I started
in hospital at how bad the systems are. I know the staff will do their very best to keep looking
after everyone, but there are no robust systems in place to deal with blackouts like this, information-sharing
is hard enough in a clinical environment when everything works.
Without the IT systems I suspect test results will be missed, and definitely delayed. Handovers
are much more difficult. It will absolutely certainly impact patient safety negatively, even if
that impact can't be clearly measured. This is basically all the result of chronic underfunding
and crap, short-sighted management.
Theresa, 44, a breast cancer patient from Lincolnshire
I was halfway through my chemotherapy infusion when the attack happened. The treatment finished
without a hitch, but I then had to wait for a couple of hours for my medications to take home.
That's because all drugs have to be checked against prescriptions, and they are all computerised.
The hospital pharmacists worked quickly to produce paper copies, but it still took a while. The
horrible side-effects (nausea, exhaustion, dizziness) kicked in while I was stuck in rush-hour
traffic coming home. Fortunately, I wasn't driving.
There were other patients in the ward waiting to start their chemo whose drugs had been delivered
but again couldn't be checked, so administration was delayed. In some cases treatment had to be
postponed entirely for another day. The oncology nurses and the hospital staff were brilliant
throughout, reassuring patients and doing their best in difficult circumstances. They were also
deeply apologetic, frustrated that they couldn't do their job, and angry that such an act had
put patients treatment – and lives – at risk.
Amber, 40, a community nurse from Essex
We have been unable to check patient information and scheduled visits for this afternoon. I am
working this weekend and had to write down who we may see tomorrow from my own memory. Our own
call centre for community services is in lockdown and unable to receive any information regarding
authorisation for drug changes or referrals. We are also unable to look up patient addresses,
complete any documentation or check test results.
Alun Phillips, 45, a community pharmacist from Merseyside
Doctors in Liverpool have been advised to isolate their computer systems from the wider NHS network.
This has left many of our local surgeries unable to access patient records, which are cloud-based.
Surgeries are unable to issue prescriptions from their systems, most of which are now issued electronically
via the NHS spine. Even if they could, we (community pharmacy) are being advised to not connect
to the spine. We have had quite a few requests from local surgeries to tell them what medication
patient are on, as although they cannot access patient records we still have our copy of the patients'
medication records. We have also made some emergency supplies of medication to patients unable
to access GP services while they are down.
Kyle, 42, a patient from Maidestone
I am waiting for test results after a urine infection and pain in my kidneys. I called the doctors
this afternoon. They said it looks like I need a further prescription but the doctor will need
to call me back. Two hours later I get a call from the doctor advising me that they have had to
shut down their systems due to this hack, and that they can't give me any results till Monday.
I am now worried that my situation is going to get worse without any treatment.
Ben, 37, in the prescription team at a GP surgery in the north
We were unable to process any prescriptions for patients, including urgent requests. As a result
patients could potentially be left without asthma, epilepsy or diabetes medication over the weekend.
We also had a medical emergency on-site and waited over 40 minutes for an ambulance to attend.
Ali, a cardiologist from the north
I am a cardiology registrar. At work, on call for a tertiary cardiology centre. Treating patients
with heart attacks, attending cardiac arrests, seeing sick patients in resus. We are unable to
access to old notes, blood results, x-rays or order vital tests. Blood samples are being sent
to other hospitals. We have one working x-ray viewer for the entire hospital and emergency results
are being rung through already overloaded phone lines. All of which potentially delays vital treatment
and could jeopardise patient safety. Those with life-threatening problems are still receiving
appropriate care. Though this couldn't have happened at a worse time with the weekend looming,
patients are still being looked after safely thanks to the dedication of all the members of staff
at work tonight. It's been a stark reminder of the conditions we worked under over 20 years ago
– and on how reliant on computers we are even to do things as simple as prescribe basic drugs.
Kaley, 30, a receptionist at a large surgery in the north-west
Friday afternoons are usually one of our busiest times at the surgery. With already full clinics
and people ringing for emergency appointments there were five reception staff on duty. There was
no warning that there was anything wrong with the computer systems but at around 3pm the screens
all went black, indicating that the computers had crashed. We had no access to any patient information
for the GPs or nurses. There was no way of checking the patients in. Phones were still ringing.
The computers were down for about an hour but then we were able to get back on. We received notification
that there was a virus affecting the whole of the NHS. The practice manager received a text from
the CCG advising that we should invoke "emergency planning measures". This involves printing lists
out of patients due to attend all clinics from Friday afternoon until Monday afternoon. Then we
had to print out full medical information for each patient as the system was being taken down
to investigate the virus. It's been a difficult afternoon.
Some names and details have been changed.
WikiLeaks
Today, May 12th 2017, WikiLeaks publishes "AfterMidnight" and "Assassin", two CIA malware frameworks
for the Microsoft Windows platform.
"AfterMidnight" allows operators to dynamically load and execute malware payloads on a target machine.
The main controller disguises as a self-persisting Windows Service DLL and provides secure execution
of "Gremlins" via a HTTPS based Listening Post (LP) system called "Octopus".
Once installed on a target machine AM will call back to a configured LP on a configurable schedule,
checking to see if there is a new plan for it to execute.
If there is, it downloads and stores all needed components before loading all new gremlins in
memory. "Gremlins" are small AM payloads that are meant to run hidden on the target and either subvert
the functionality of targeted software, survey the target (including data exfiltration) or provide
internal services for other gremlins.
The special payload "AlphaGremlin" even has a custom script language which allows operators to
schedule custom tasks to be executed on the target machine.
"Assassin" is a similar kind of malware; it is an automated implant that provides a simple collection
platform on remote computers running the Microsoft Windows operating system. Once the tool is installed
on the target, the implant is run within a Windows service process. "Assassin" (just like "AfterMidnight")
will then periodically beacon to its configured listening post(s) to request tasking and deliver
results.
Communication occurs over one or more transport protocols as configured before or during deployment.
The "Assassin" C2 (Command and Control) and LP (Listening Post) subsystems are referred to collectively
as" The Gibson" and allow operators to perform specific tasks on an infected target..
Documents:
https://wikileaks.org/vault7/#AfterMidnight
...The Barts Health Group, which helps manage some of the largest hospitals in London, said, "
We are experiencing a major IT disruption and there are delays at all of our hospitals. "
Patients had to be turned away from surgeries and appointments at medical facilities throughout
England, and ambulances had to be rerouted to other hospitals as well.
Telefonica, one of the largest telecommunications companies in Spain, was one target, though their
services and clients were not affected, as the malicious software only impacted certain computers
on an internal network.
Full report:
https://sputniknews.com/europe/201705121053564741-cyber-attack-targets-institutions-worldwide/
(vice.com)
49 Posted by EditorDavid on Saturday May 13, 2017 @06:57PM from the wanna-cry-more? dept.
Remember that "kill switch" which
shut down the WannCry ransomware? An anonymous reader quotes Motherboard: Over Friday and
Saturday, samples of the malware emerged without that debilitating feature, meaning that
attackers may be able to resume spreading ransomware even though a security researcher cut off
the original wave. "I can confirm we've had versions without the kill switch domain connect since
yesterday," Costin Raiu, director of global research and analysis team at Kaspersky Lab told Motherboard
on Saturday... Another researcher confirmed they have seen samples of the malware without the killswitch.
Notable quotes:
"... Email is one of the main infection methods. Be wary of unexpected emails especially if they contain links and/or attachments. ..."
- Email is one of the main infection methods. Be wary of unexpected emails especially if
they contain links and/or attachments.
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros
to view its content. Unless you are absolutely sure that this is a genuine email from a trusted
source, do not enable macros and instead immediately delete the email.
- Backing up important data is the single most effective way of combating ransomware infection.
Attackers have leverage over their victims by encrypting valuable files and leaving them inaccessible.
If the victim has backup copies, they can restore their files once the infection has been cleaned
up. However organizations should ensure that back-ups are appropriately protected or stored off-line
so that attackers can't delete them.
- Using cloud services could help mitigate ransomware infection, since many retain previous
versions of files, allowing you to "roll back" to the unencrypted form.
After encryption the Trojan then deletes the shadow copies of the encrypted files.
The Trojan drops the following files in every folder where files are encrypted:
•!WannaDecryptor!.exe.lnk
•!Please Read Me!.txt
The contents of the !Please Read Me!.txt is a text version of the ransom note with details of
how to pay the ransom.
The Trojan downloads Tor and uses it to connect to a server using the Tor network.
It then displays a ransom note explaining to the user what has happened and how to pay the ransom.
WannaCry encrypts files with the following extensions, appending .WCRY to the end of the file
name:
- .123
- .3dm
- .3ds
- .3g2
- .3gp
- .602
- .7z
- .ARC
- .PAQ
- .accdb
- .aes
- .ai
- .asc
- .asf
- .asm
- .asp
- .avi
- .backup
- .bak
- .bat
- .bmp
- .brd
- .bz2
- .cgm
- .class
- .cmd
- .cpp
- .crt
- .cs
- .csr
- .csv
- .db
- .dbf
- .dch
- .der
- .dif
- .dip
- .djvu
- .doc
- .docb
- .docm
- .docx
- .dot
- .dotm
- .dotx
- .dwg
- .edb
- .eml
- .fla
- .flv
- .frm
- .gif
- .gpg
- .gz
- .hwp
- .ibd
- .iso
- .jar
- .java
- .jpeg
- .jpg
- .js
- .jsp
- .key
- .lay
- .lay6
- .ldf
- .m3u
- .m4u
- .max
- .mdb
- .mdf
- .mid
- .mkv
- .mml
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .msg
- .myd
- .myi
- .nef
- .odb
- .odg
- .odp
- .ods
- .odt
- .onetoc2
- .ost
- .otg
- .otp
- .ots
- .ott
- .p12
- .pas
- .pdf
- .pem
- .pfx
- .php
- .pl
- .png
- .pot
- .potm
- .potx
- .ppam
- .pps
- .ppsm
- .ppsx
- .ppt
- .pptm
- .pptx
- .ps1
- .psd
- .pst
- .rar
- .raw
- .rb
- .rtf
- .sch
- .sh
- .sldm
- .sldx
- .slk
- .sln
- .snt
- .sql
- .sqlite3
- .sqlitedb
- .stc
- .std
- .sti
- .stw
- .suo
- .svg
- .swf
- .sxc
- .sxd
- .sxi
- .sxm
- .sxw
- .tar
- .tbk
- .tgz
- .tif
- .tiff
- .txt
- .uop
- .uot
- .vb
- .vbs
- .vcd
- .vdi
- .vmdk
- .vmx
- .vob
- .vsd
- .vsdx
- .wav
- .wb2
- .wk1
- .wks
- .wma
- .wmv
- .xlc
- .xlm
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xlt
- .xltm
- .xltx
- .xlw
- .zip
Probably the best description of the worm on Youtube as of May 13, 2017...
Andy Beez, 9 hours ago
Thanks for the forensic deconstruction - a lot more info than the experts on Sky News!
Is it interesting the popup is written in accurate English with the correct use of capitals, commas
and full stops? Plus the grammar is correct. I understand the Italian version has the same grammatical
exactness. So not script kiddies from Chindia? This writers are well educated.
Anton, 10 hours ago
A kill switch already has been found in the code, which prevents new infections. This has been
activated by researchers and should slow the spread.
Colin Hardy, 8 hours ago
agree. Firstly, contain your network (block affected ports in/outbound), also look for compromised
hosts on your network using the various IOCs from the likes of Virus Total and other analysts
blogs. Remediate the machines, and rebuild the network - slowly, carefully and under good supervision!
Colin Hardy, 8 hours ago
this was an awesome find as well. see my new video https://youtu.be/d56g3wahBck
on how you can see it for yourself.
Symantec provides a better description of what you need to look at.
The WannaCry ransomware received and analyzed by US-CERT is a loader that contains an AES-encrypted
DLL. During runtime, the loader writes a file to disk named "t.wry". The malware then uses an embedded
128-bit key to decrypt this file. This DLL, which is then loaded into the parent process, is the
actual Wanna Cry Ransomware responsible for encrypting the user's files. Using this cryptographic
loading method, the WannaCry DLL is never directly exposed on disk and not vulnerable to antivirus
software scans.
The newly loaded DLL immediately begins encrypting files on the victim's system and encrypts the
user's files with 128-bit AES. A random key is generated for the encryption of each file.
The malware also attempts to access the IPC$ shares and SMB resources the victim system has access
to. This access permits the malware to spread itself laterally on a compromised network. However,
the malware never attempts to attain a password from the victim's account in order to access the
IPC$ share.
This malware is designed to spread laterally on a network by gaining unauthorized access to the
IPC$ share on network resources on the network on which it is operating.
References
- Malwarebytes LABS: "WanaCrypt0r ransomware hits it big just before the weekend
- Malwarebytes LABS: "The worm that spreads WanaCrypt0r"
- Microsoft: "Microsoft Security Bulletin MS17-010"
- Forbes: "An NSA Cyber Weapon Might Be Behind A Massive Global Ransomware Outbreak"
- Reuters: "Factbox: Don't click - What is the 'ransomware' WannaCry worm?"
- GitHubGist: "WannaCry|WannaDecrypt0r NSA-Cybereweapon-Powered Ransomware Worm"
Notable quotes:
"... This vulnerability was patched in the Microsoft March update (MS17-010) ..."
"... Ensure that port 445 is blocked for firewall communications with all exceptions scrutinized and verified before adding. ..."
WanaCryptor 2.0, WannaCry, WCry or WCryp is currently a world-wide ransom-ware outbreak. These
are all versions of Crypto-locker, encrypting victim files and demanding payment via bit-coin.
This vulnerability was patched in the Microsoft March update (MS17-010).
The following links contain information about the exploit that the new malware is using (based
on ETERNAL BLUE) and the fix and temporary workaround for servers and local clients, as well as firewall
configuration recommendations.
SMB v1 is the current exploit mechanism being used for moving within enterprise. Movement has been
detected from Cloud Sync file-share as well. The link contains information on disabling SMBv1 (which
is the only recommended service to disable) via Servers, Powershell, and local Client Firewall Configuration,
Ensure that port 445 is blocked for firewall communications with all exceptions scrutinized
and verified before adding.
India was among the countries worst affected by the Wanna Cry attack, data shared by Kaspersky,
a Russian anti-virus company, showed. According to initial calculations performed soon after the
malware struck on Friday night, around five per cent of all computers affected in the attack were
in India.
Mikko Hypponen, chief research officer at a Helsinki-based cyber security company called F-Secure,
told news agency AFP that the it was the biggest ransomware outbreak in history and estimated that
130,000 systems in more than 100 countries had been affected.
Hypponen added that Russia and India were hit particularly hard, largely because Microsoft's Windows
XP - one of the operating systems most at risk - was still widely used there.
WanaCrypt0r has been most effective-not only does the ransomware loop through every open RDP session
on a system and run the ransomware as that user, but the initial component that gets dropped on systems
appears to be a worm that contains and runs the ransomware, spreading itself using the ETERNALBLUE
SMB vulnerability (
MS17-010
).
The WinMain of this
executable first tries to connect to the website www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com.
It doesn't actually download anything there, just tries to connect. If the connection succeeds,
the binary exits.
This was probably some kind of kill switch or anti-sandbox technique. Whichever it is, it has
backfired on the authors of the worm, as the domain has been sinkholed and the host in question now
resolves to an IP address that hosts a website. Therefore, nothing will happen on any new systems
that runs the executable. This only applies to the binary with the hash listed above; there may well
be new versions released in the future. UPDATE: The second argument to InternetOpenA is 1 (INTERNET_OPEN_TYPE_DIRECT),
so the worm will still work on any system that requires a proxy to access the Internet, which is
the case on the majority of corporate networks.
... ... ...
[after kill switch check pass] ...
the first thing the worm does is check the number of arguments it was launched with. If it was run
with less than two arguments passed, it installs a service called mssecsvc2.0 with display
name Microsoft Security Center (2.0) Service (where the binary ran is itself with two
arguments), starts that service, drops the ransomware binary located in the resources of the worm,
and runs it.
If it was run with two arguments or more-in other words, if it was run as a service-execution
eventually falls through to the worm function.
This from the author "accidental kill switch discovery" : "I was able to set up a live tracking
map and push it out via twitter (you can still see it
here )." Fascinating...
As of May 13 9 PM worm is still spreading with the date probably a hundred hits per hour, but kill
switch prevents newly found instances from running their own instance of the worm. An interesting
side effect is that if network has proxy that prevent access the kill switch domain then the work will
spread at full speed. So propagation into proxied network with an isolated root server
network can lead to increase in the worm infection rate as kill switch site will not work.
In other words the work is the most dangerous for private networks with the private DNS root.
Notable quotes:
"... When I returned home at about 2:30, the threat sharing platform was flooded with posts about various NHS systems all across the country being hit, which was what tipped me of to the fact this was something big. ..."
"... contrary to popular belief, most NHS employees don't open phishing emails which suggested that something to be this widespread it would have to be propagated using another method) ..."
"... Using Cisco Umbrella, we can actually see query volume to the domain prior to my registration of it which shows the campaign started at around 8 AM UTC. ..."
"... more interestingly was that after encrypting the fake files I left there as a test, it started connecting out to random IP addresses on port 445 (used by SMB). ..."
"... The mass connection attempts immediately made me think exploit scanner, and the fact it was scanning on the SMB port caused me to look back to the recent ShadowBroker leak of NSA exploits containing .an SMB exploit. ..."
So finally I've found enough time between emails and Skype calls to write up on the crazy events
which occurred over Friday, which was supposed to be part of my week off (I made it a total of 4
days without working, so there's that). You've probably read about the WannaCrypt fiasco on several
news sites, but I figured I'd tell my story.
I woke up at around 10 AM and checked onto the UK cyber threat sharing platform where i had been
following the spread of the Emotet banking malware, something which seemed incredibly significant
until today. There were a few of your usual posts about various organisations being hit with ransomware,
but nothing significant yet. I ended up going out to lunch with a friend, meanwhile the WannaCrypt
ransomware campaign had entered full swing.
When I returned home at about 2:30, the threat sharing platform was flooded with posts about various
NHS systems all across the country being hit, which was what tipped me of to the fact this was something
big.
Although ransomware on a public sector system isn't even newsworthy, systems being hit simultaneously
across the country is (contrary to popular belief, most NHS employees don't open phishing emails
which suggested that something to be this widespread it would have to be propagated using another
method). I was quickly able to get a sample of the malware with the help of Kafeine, a good friend
and fellow researcher.
Upon running the sample in my analysis environment I instantly noticed it
queried an unregistered domain, which i promptly registered.
Using Cisco Umbrella, we can actually see query volume to the domain prior to my registration
of it which shows the campaign started at around 8 AM UTC.
... ... ...
While the domain was propagating, I ran the sample again in my virtual environment to be met with
WannaCrypt ransom page; but more interestingly was that after encrypting the fake files I left there
as a test, it started connecting out to random IP addresses on port 445 (used by SMB).
The mass
connection attempts immediately made me think exploit scanner, and the fact it was scanning on the
SMB port caused me to look back to the recent ShadowBroker leak of NSA exploits containing .an SMB
exploit. Obvious I had no evidence yet that it was definitely scanning SMB hosts or using the
leaked NSA exploit, so I tweeted out my finding and went to tend to the now propagated domain.
... ... ...
Now one thing that's important to note is the actual registration of the domain was not on a whim.
My job is to look for ways we can track and potentially stop botnets (and other kinds of malware),
so I'm always on the lookout to pick up unregistered malware control server (C2) domains. In fact
I registered several thousand of such domains in the past year.
Our standard model goes something like this.
- Look for unregistered or expired C2 domains belonging to active botnets and point it to our
sinkhole (a sinkhole is a server designed to capture malicious traffic and prevent control of
infected computers by the criminals who infected them).
- Gather data on the geographical distribution and scale of the infections, including IP addresses,
which can be used to notify victims that they're infected and assist law enforcement.
- Reverse engineer the malware and see if there are any vulnerabilities in the code which would
allow us to take-over the malware/botnet and prevent the spread or malicious use, via the domain
we registered.
In the case of WannaCrypt, step 1, 2 and 3 were all one and the same, I just didn't know it yet.
A few seconds after the domain had gone live I received a DM from a Talos analyst asking for the
sample I had which was scanning SMB host, which i provided. Humorously at this point we had unknowingly
killed the malware so there was much confusion as to why he could not run the exact same sample I
just ran and get any results at all. As curious as this was, I was pressed for time and wasn't able
to investigate, because now the sinkhole servers were coming dangerously close to their maximum load.
I set about making sure our sinkhole server were stable and getting the expected data from the
domain we had registered (at this point we still didn't know much about what the domain I registered
was for, just that anyone infected with this malware would connect to the domain we now own, allowing
us to track the spread of the infection). Sorting out the sinkholes took longer than expected due
to a very large botnet we had sinkholed the previous week eating up all the bandwidth, but soon enough
I was able to set up a live tracking map and push it out via twitter (you can still see it
here ).
Aris Adamantiadis > greggreen29 • 12 hours ago
To be fair, he said himself he thought at some point that registering the domain name triggered
the ransomware instead of disabling it. The story headline would have mentioned "Security research
accidentally armed a ransomware" in that case. His experience told him it was a good thing to
own domains used by C&C, his luck made it that it was a kill switch. I don't think "accidental"
is undeserved in this case.
Whatever, it's good job!
Dave > greggreen29 • 13 hours ago
The media is filled with people who don't do their research. This is both true in the IT world
along with the firearms world. Me being involved in both. Media however LOVES buzzwords without
even knowing what that word means nor use it in context correctly.
They make conclusions about things they don't even understand or refer to a real expert in
the field or multiple to get out of single sourced subjective analysis problems.
I am no total expert in either though I do know a lot, but I make my due diligience if I do
write aboit a subject, I do RESEARCH vs WEBSEARCH on it to draw conclusions. I also then employ
logic and personal experiences for supplimenting those conclusions if I have the experiences to
draw upon.
This is why I follow people I would deem as experts in the field, to learn more about what
we come across, to ask questions, and to constantly learn.
This is why I follow the Malwaretech crew and others like them in security and forensics.
Malwaretech, thank you for your service, not only for this incident, but all the research you
do.
Susan O'neill > Dave • 10 hours ago
Well said Dave. Whilst I struggled to follow the report on his progress, it would seem that
he is connected to people who can offer a service and using his own expertise and by a process
of elimination, find the answers, but because he caught on to something very quickly(which he
might easily have missed, had he not been so thorough and alert) would have allowed the worm to
continue it's travels. I think a lot of people should be very thankful to MalwareTech and his
expertise - even if it does generate more business for him, it's probably well deserved.
How to enable or disable SMB protocols on the SMB server 0 -- Windows 8 and Windows Server
2012 Windows 8 and Windows Server 2012 introduce the new Set-SMBServerConfiguration Windows PowerShell
cmdlet. The cmdlet enables you to enable or disable the SMBv1, SMBv2, and SMBv3 protocols on the
server component.
Notes When you enable or disable SMBv2 in Windows 8 or in Windows Server 2012, SMBv3 is also enabled
or disabled. This behavior occurs because these protocols share the same stack.
You do not have to restart the computer after you run the Set-SMBServerConfiguration cmdlet.
- To obtain the current state of the SMB server protocol configuration, run the following cmdlet:
Get-SmbServerConfiguration | Select EnableSMB1Protocol, EnableSMB2Protocol
- To disable SMBv1 on the SMB server, run the following cmdlet: Set-SmbServerConfiguration -EnableSMB1Protocol
$false
... ... ...
Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008 To enable or disable
SMB protocols on an SMB Server that is running Windows 7, Windows Server 2008 R2, Windows Vista,
or Windows Server 2008, use Windows PowerShell or Registry Editor. Windows PowerShell 2.0 or a
later version of PowerShell
- To disable SMBv1 on the SMB server, run the following cmdlet: Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters"
SMB1 -Type DWORD -Value 0 -Force
... ... ...
Note You must restart the computer after you make these changes. Registry Editor Important
This article contains information about how to modify the registry. Make sure that you back up the
registry before you modify it. Make sure that you know how to restore the registry if a problem occurs.
For more information about how to back up, restore, and modify the registry, click the following
article number to view the article in the Microsoft Knowledge Base:
322756 How to back
up and restore the registry in Windows To enable or disable SMBv1 on the SMB server, configure the
following registry key: Registry subkey:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Registry entry: SMB1
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
For customers using Windows Defender, Microsoft released an update on May 13 which detects this
threat as
Ransom:Win32/WannaCrypt.
Defensive firewall configuration is important as Windows is full of holes. Download the update
here
Notable quotes:
"... This security update is rated Critical for all supported releases of Microsoft Windows. ..."
This is the vulnerability that Wanna Cry malware uses
March 14, 2017 Published: March 14, 2017
Version: 1.0
This security update is rated Critical for all supported releases of Microsoft Windows.
For more information, see the Affected Software and Vulnerability Severity Ratings section.
The security update addresses the vulnerabilities by correcting how SMBv1 handles specially
crafted requests.
For more information about the vulnerabilities, see the Vulnerability Information section.
For more information about this update, see
Microsoft Knowledge Base Article
4013389 .
In mid-April, an arsenal of powerful software tools apparently designed by the NSA to infect and
control Windows computers was leaked by an entity known only as the "Shadow Brokers." Not even a
whole month later, the hypothetical threat that criminals would use the tools against the general
public has become real, and tens of thousands of computers worldwide are now crippled by an unknown
party demanding ransom.
The malware worm taking over the computers goes by the names "WannaCry" or "Wanna Decryptor."
It spreads from machine to machine silently and remains invisible to users until it unveils itself
as so-called ransomware, telling users that all their files have been encrypted with a key known
only to the attacker and that they will be locked out until they pay $300 to an anonymous party using
the cryptocurrency Bitcoin.
At this point, one's computer would be rendered useless for anything other than paying said ransom.
The price rises to $600 after a few days; after seven days, if no ransom is paid, the hacker (or
hackers) will make the data permanently inaccessible (WannaCry victims will have a handy countdown
clock to see exactly how much time they have left).
Ransomware is not new; for victims, such an attack is normally a colossal headache. But today's
vicious outbreak has spread ransomware on a massive scale, hitting not just home computers but reportedly
health care, communications infrastructure, logistics, and government entities.
Full report:
https://theintercept.com/2017/05/12/the-nsas-lost-digital-weapon-is-helping-hijack-computers-around-the-world/
Cyber attacks on a global scale took place on Friday, May 12, 2017. The notable hits include computers
in 16 UK hospitals, Telefonica Telecom in Spain, Gas Natural, Iberdrola. Several thousand computer were
infected in 99 countries.
WannaCry ransomware attack - Wikipedia
WannaCry is believed to use the
EternalBlue
exploit, which
was developed by the U.S.
National Security Agency[15][16]
to attack computers running
Microsoft Windows operating
systems. Once it invades a network, it is self-replicated and transmitted to other computers.
Initial infection vector is either via
LAN, an email attachment, or drive-by
download.
A kill switch has been found
in the code, which since May 13 helps to prevent new infections. This swich was accidentally activated
by an anti-virus researcher from GB. However, different versions of the attack may be released and all
vulnerable systems still have an urgent need to be patched.
Notable quotes:
"... Hollywood Overwhelmed With Hack Attacks; FBI Advises 'Pay Ransom'... ..."
The ransomware has been identifed as WannaCry
* * *
Update 4 : According to experts tracking and analyzing the worm and its spread, this could
be one of the worst-ever recorded attacks of its kind .
The security researcher who tweets and blogs as MalwareTech
told The Intercept "I've never seen anything like this with ransomware," and "the last worm
of this degree I can remember is Conficker." Conficker was a notorious Windows worm first spotted
in 2008; it went on to infect over nine million computers in nearly 200 countries.
As The Intercept details,
Today's WannaCry attack appears to use an NSA exploit codenamed ETERNALBLUE, a software weapon
that would have allowed the spy agency's hackers to break into any of millions of Windows computers
by exploiting a flaw in how certain version of Windows implemented a network protocol commonly
used to share files and to print. Even though Microsoft fixed the ETERNALBLUE vulnerability in
a March software update, the safety provided there relied on computer users keeping their systems
current with the most recent updates. Clearly, as has always been the case, many people (including
in governments) are not installing updates. Before, there would have been some solace in knowing
that only enemies of the NSA would have to fear having ETERNALBLUE used against them–but from
the moment the agency lost control of its own exploit last summer, there's been no such assurance.
Today shows exactly what's at stake when government hackers can't keep their virtual weapons
locked up.
As security researcher Matthew Hickey, who tracked the leaked NSA tools last month, put it,
"I am actually surprised that a weaponized malware of this nature didn't spread sooner."
Update 3: Microsoft has issued a statement, confirming the status the vulnerability:
Today our engineers added detection and protection against new malicious software known as
Ransom:Win32.WannaCrypt.
In March, we provided a security update which provides additional protections against this
potential attack.
Those who are running our free antivirus software and have Windows updates enabled, are protected.
We are working with customers to provide additional assistance.
Update 2: Security firm
Kaspersky Lab has recorded more than 45,000 attacks in 74 countries in the past 10 hours
Seventy-four countries around the globe have been affected, with the number of victims still
growing, according to Kaspersky Lab. According to Avast, over 57,000 attacks have been detected
worldwide, the company said, adding that it "quickly escalated into a massive spreading."
57,000 detections of
#WannaCry (aka
#WanaCypt0r aka
#WCry )
#ransomware by Avast
today. More details in blog post: https://t.co/PWxbs8LZkk
- Jakub Kroustek (@JakubKroustek)
May 12,
2017
According to Avast, the ransomware has also targeted Russia, Ukraine and Taiwan. The virus
is apparently the upgraded version of the ransomware that first appeared in February. Believed
to be affecting only Windows operated computers, it changes the affected file extension names
to ".WNCRY." It then drops ransom notes to a user in a text file, demanding $300 worth of bitcoins
to be paid to unlock the infected files within a certain period of time.
While the victim's wallpaper is being changed, affected users also see a countdown timer to
remind them of the limited time they have to pay the ransom. If they fail to pay, their data will
be deleted, cybercriminals warn. According to the New York Times, citing security experts, the
ransomware exploits a "vulnerability that was discovered and developed by the National Security
Agency (NSA)." The hacking tool was leaked by a group calling itself the Shadow Brokers, the report
said, adding, that it has been distributing the stolen NSA hacking tools online since last year.
Predictably, Edward Snowden - who has been warning about just such an eventuality - chimed
in on
Twitter, saying " Whoa: @NSAGov decision to build attack tools targeting US software now threatens
the lives of hospital patients."
* * *
Update 1 : In a shocking revelation,
The FT reports that hackers responsible for the wave of cyber attacks that struck organisations
across the globe used tools stolen from the US National Security Agency.
A hacking tool known as "eternal blue", developed by US spies has been weaponised by the hackers
to super-charge an existing form of ransomware known as WannaCry, three senior cyber security
analysts said. Their reading of events was confirmed by western security officials who are still
scrambling to contain the spread of the attack. The NSA's eternal blue exploit allows the malware
to spread through file-sharing protocols set up across organisations, many of which span the globe.
As Sam Coates summed up...
NHS hack: So NSA had secret backdoor into Windows. Details leaked few weeks ago. Now backdoor
being exploited by random criminals. Nightmare
- Sam Coates Times (@SamCoatesTimes)
May 12,
2017
* * *
We earlier reported in the disturbing fact that
hospitals across the United Kingdom had gone dark due to a massive cyber-attack...
Hospitals across the UK have been hit by what appears to be a major, nationwide cyber-attack,
resulting in the loss of phonelines and computers, with many hospitals going "dark" and some diverting
all but emergency patients elsewhere. At some hospitals patients are being told not to come to A&E
with all non-urgent operations cancelled, the
BBC reports .
The UK National Health Service said: "We're aware that a number of trusts that have reported potential
issues to the CareCERT team. We believe it to be ransomware ." It added that trusts and hospitals
in London, Blackburn, Nottingham, Cumbria and Hertfordshire have been affected and are reporting
IT failures, in some cases meaning there is no way of operating phones or computers.
At Lister Hospital in Stevenage, the telephone and computer system has been fully disabled in
an attempt to fend off the attack .
NHS England says it is aware of the issue and is looking into it.
UK Prime Minister Theresa May confirms today's massive cyber hit on NHS is part of wider international
attack and there is no evidence patient data has been compromised.
Hospitals say backlog will go on for some weeks after today's cyber attack
#NHScyberattack
pic.twitter.com/BGV5jV7KZ1
- Sky News Tonight (@SkyNewsTonight)
May 12, 2017
The situation has got significantly worse as
The BBC reports the ransomware
attack has gone global.
Screenshots of a well known program that locks computers and demands a payment in Bitcoin have
been shared online by parties claiming to be affected.
Manthong
macholatte
May 12, 2017 2:19 PM
"Ransomware"?
The FBI has the solution and comes to the rescue .
Hollywood Overwhelmed With Hack Attacks; FBI Advises 'Pay Ransom'...
Manthong
Manthong
May 12, 2017 2:22 PM
It's just a damn good thing the US spent all that time and money developing all that stuff.
Now that it's out, just pay the ransom to the Cyber-Barbary Pirates so that the government
can return to its main 1984 mass surveillance and control mission.
stormsailor
pods
May 12, 2017 4:52 PM
My son is an IT professional and has been inundated with new clients calling to rid their complex
systems of this plague.For his clients he has divised protection from it, but most of the calls
he gets are from large hospitals, corporations, etc. that have their own IT staff.He can fix
it and prevent/firewall it so it doesn't happen but some of the systems are so complex with so
many open ends, his bill is sometimes as much as the hackers are asking for. He told me that in
some cases he is tempted to tell them to just pay it, however, he said all of the payoffs have
to be made with bitcoin on the "dark-web" and since you are dealing with known criminals he has
heard that more than half the time they do not fix it.
He was in New Orleans about a month ago, Thursday through Sunday clearing up a large companies
servers and systems, worked 70 hours and billed them 24k plus expenses
virgule
Arnold
May 12, 2017 3:21 PM
First thing I suggest to do if this happens to you, is to shut down your computer, take out the
HD, and boot it into a Linux system, so at least you can make a copy in a asafe environment, before
things get worse.
The article was published at 12:16 EDT so the work probably was unleashed at least 24 hours before
that
The ransomware uses a vulnerability first revealed to the public as part of a leaked stash of
NSA-related documents in order to infect Windows PCs and encrypt their contents, before demanding
payments of hundreds of dollars for the key to decrypt files.
How does it spread?
Most ransomware is spread hidden within Word documents, PDFs and other files normally sent via
email, or through a secondary infection on computers already affected by viruses that offer a back
door for further attacks.
MalwareHunterTeam (@malwrhunterteam)
There is a new version of WCry/WannaCry ransomware: "WanaCrypt0r 2.0".
Extension: .WNCRY
Note: @[email protected] @BleepinComputer
pic.twitter.com/tdq0OBScz4
May 12,
2017
What is WanaCrypt0r 2.0?
The malware that has affected Telefónica in Spain and the NHS in Britain is the same software:
a piece of ransomware first spotted in the wild
by security
researchers MalwareHunterTeam , at 9:45am on 12 May.
Less than four hours later, the ransomware had infected NHS computers, albeit
originally only in Lancashire , and spread laterally throughout the NHS's internal network. It
is also being called Wanna Decryptor 2.0, WCry 2, WannaCry 2 and Wanna Decryptor 2.
How much are they asking for?
WanaCrypt0r 2.0 is asking for $300 worth of the cryptocurrency Bitcoin to unlock the contents
of the computers.
Myles Longfield (@myleslongfield)
Shocking that our @NHS is under attack
and being held to ransom.
#nhscyberattack
pic.twitter.com/1bcrqD9vEz
May 12,
2017
Who are they?
The creators of this piece of ransomware are still unknown, but WanaCrypt0r 2.0 is their second
attempt at cyber-extortion. An earlier version, named WeCry, was
discovered
back in February this year : it asked users for 0.1 bitcoin (currently worth $177, but with a
fluctuating value) to unlock files and programs.
How is the NSA tied in to this attack?
Once one user has unwittingly installed this particular flavour of ransomware on their own PC,
it tries to spread to other computers in the same network. In order to do so, WanaCrypt0r uses a
known vulnerability in the Windows operating system, jumping between PC and PC. This weakness was
first revealed to the world as part of
a huge leak of NSA hacking tools and known weaknesses by an anonymous group calling itself "Shadow
Brokers" in April.
Was there any defence?
Yes. Shortly before the Shadow Brokers released their files, Microsoft issued a patch for affected
versions of Windows, ensuring that the vulnerability couldn't be used to spread malware between fully
updated versions of its operating system. But for many reasons, from lack of resources to a desire
to fully test new updates before pushing them out more widely, organisations are often slow to install
such security updates on a wide scale.
Who are the Shadow Brokers? Were they behind this attack?
In keeping with almost everything else in the world of cyberwarfare, attribution is tricky. But
it seems unlikely that the Shadow Brokers were directly involved in the ransomware strike: instead,
some opportunist developer seems to have spotted the utility of the information in the leaked files,
and updated their own software accordingly. As for the Shadow Brokers themselves, no-one really knows,
but fingers point towards Russian actors as likely culprits.
Will paying the ransom really unlock the files?
Sometimes paying the ransom will work, but sometimes it won't. For the
Cryptolocker ransomware that hit a few years ago, some users reported that they really did get
their data back after paying the ransom, which was typically around £300. But there's no guarantee
paying will work, because cybercriminals aren't exactly the most trustworthy group of people.
There are also a collection of viruses that go out of their way to look like ransomware such as
Cryptolocker, but which won't hand back the data if victims pay. Plus, there's the ethical issue:
paying the ransom funds more crime.
What else can I do?
Once ransomware has encrypted your files there's not a lot you can do. If you have a backup of
the files you should be able to restore them after cleaning the computer, but if not your files could
be gone for good.
Some badly designed ransomware, however, has been itself hacked by security researchers, allowing
recovery of data. But such situations are rare, and tend not to apply in the case of widescale professional
hits like the WanaCrypt0r attack.
How long will this attack last?
Ransomware often has a short shelf life. As anti-virus vendors cotton on to new versions of the
malware, they are able to prevent infections originating and spreading, leading to developers attempting
"Big Bang" introductions like the one currently underway.
Will they get away with it?
Bitcoin, the payment medium through which the hackers are demanding payment, is difficult to trace,
but not impossible, and the sheer scale of the attack means that law enforcement in multiple countries
will be looking to see if they can follow the money back to the culprits.
Why is the NHS being targeted?
The NHS does not seem to have been specifically targeted, but the service is not helped by its
reliance on old, unsupported software. Many NHS trusts still use Windows XP, a version of Microsoft's
operating system that has not received publicly available security updates for half a decade, and
even those which are running on newer operating systems are often sporadically maintained. For an
attack which relies on using a hole fixed less than three months ago, just a slight oversight can
be catastrophic.
Attacks on healthcare providers across the world are at an all-time high as they contain valuable
private information, including healthcare records.
Ransomware threat on the rise as 'almost 40% of businesses attacked'
Softpanorama Recommended
Useful Youtube video (most are promotional junk or click baits)
Useful articles
Ransomware
Cryptovirology
DNS
Group policy info
Technical descriptions
Society
Groupthink :
Two Party System
as Polyarchy :
Corruption of Regulators :
Bureaucracies :
Understanding Micromanagers
and Control Freaks : Toxic Managers :
Harvard Mafia :
Diplomatic Communication
: Surviving a Bad Performance
Review : Insufficient Retirement Funds as
Immanent Problem of Neoliberal Regime : PseudoScience :
Who Rules America :
Neoliberalism
: The Iron
Law of Oligarchy :
Libertarian Philosophy
Quotes
War and Peace
: Skeptical
Finance : John
Kenneth Galbraith :Talleyrand :
Oscar Wilde :
Otto Von Bismarck :
Keynes :
George Carlin :
Skeptics :
Propaganda : SE
quotes : Language Design and Programming Quotes :
Random IT-related quotes :
Somerset Maugham :
Marcus Aurelius :
Kurt Vonnegut :
Eric Hoffer :
Winston Churchill :
Napoleon Bonaparte :
Ambrose Bierce :
Bernard Shaw :
Mark Twain Quotes
Bulletin:
Vol 25, No.12 (December, 2013) Rational Fools vs. Efficient Crooks The efficient
markets hypothesis :
Political Skeptic Bulletin, 2013 :
Unemployment Bulletin, 2010 :
Vol 23, No.10
(October, 2011) An observation about corporate security departments :
Slightly Skeptical Euromaydan Chronicles, June 2014 :
Greenspan legacy bulletin, 2008 :
Vol 25, No.10 (October, 2013) Cryptolocker Trojan
(Win32/Crilock.A) :
Vol 25, No.08 (August, 2013) Cloud providers
as intelligence collection hubs :
Financial Humor Bulletin, 2010 :
Inequality Bulletin, 2009 :
Financial Humor Bulletin, 2008 :
Copyleft Problems
Bulletin, 2004 :
Financial Humor Bulletin, 2011 :
Energy Bulletin, 2010 :
Malware Protection Bulletin, 2010 : Vol 26,
No.1 (January, 2013) Object-Oriented Cult :
Political Skeptic Bulletin, 2011 :
Vol 23, No.11 (November, 2011) Softpanorama classification
of sysadmin horror stories : Vol 25, No.05
(May, 2013) Corporate bullshit as a communication method :
Vol 25, No.06 (June, 2013) A Note on the Relationship of Brooks Law and Conway Law
History:
Fifty glorious years (1950-2000):
the triumph of the US computer engineering :
Donald Knuth : TAoCP
and its Influence of Computer Science : Richard Stallman
: Linus Torvalds :
Larry Wall :
John K. Ousterhout :
CTSS : Multix OS Unix
History : Unix shell history :
VI editor :
History of pipes concept :
Solaris : MS DOS
: Programming Languages History :
PL/1 : Simula 67 :
C :
History of GCC development :
Scripting Languages :
Perl history :
OS History : Mail :
DNS : SSH
: CPU Instruction Sets :
SPARC systems 1987-2006 :
Norton Commander :
Norton Utilities :
Norton Ghost :
Frontpage history :
Malware Defense History :
GNU Screen :
OSS early history
Classic books:
The Peter
Principle : Parkinson
Law : 1984 :
The Mythical Man-Month :
How to Solve It by George Polya :
The Art of Computer Programming :
The Elements of Programming Style :
The Unix Hater’s Handbook :
The Jargon file :
The True Believer :
Programming Pearls :
The Good Soldier Svejk :
The Power Elite
Most popular humor pages:
Manifest of the Softpanorama IT Slacker Society :
Ten Commandments
of the IT Slackers Society : Computer Humor Collection
: BSD Logo Story :
The Cuckoo's Egg :
IT Slang : C++ Humor
: ARE YOU A BBS ADDICT? :
The Perl Purity Test :
Object oriented programmers of all nations
: Financial Humor :
Financial Humor Bulletin,
2008 : Financial
Humor Bulletin, 2010 : The Most Comprehensive Collection of Editor-related
Humor : Programming Language Humor :
Goldman Sachs related humor :
Greenspan humor : C Humor :
Scripting Humor :
Real Programmers Humor :
Web Humor : GPL-related Humor
: OFM Humor :
Politically Incorrect Humor :
IDS Humor :
"Linux Sucks" Humor : Russian
Musical Humor : Best Russian Programmer
Humor : Microsoft plans to buy Catholic Church
: Richard Stallman Related Humor :
Admin Humor : Perl-related
Humor : Linus Torvalds Related
humor : PseudoScience Related Humor :
Networking Humor :
Shell Humor :
Financial Humor Bulletin,
2011 : Financial
Humor Bulletin, 2012 :
Financial Humor Bulletin,
2013 : Java Humor : Software
Engineering Humor : Sun Solaris Related Humor :
Education Humor : IBM
Humor : Assembler-related Humor :
VIM Humor : Computer
Viruses Humor : Bright tomorrow is rescheduled
to a day after tomorrow : Classic Computer
Humor
The Last but not Least Technology is dominated by
two types of people: those who understand what they do not manage and those who manage what they do not understand ~Archibald Putt.
Ph.D
Copyright © 1996-2021 by Softpanorama Society. www.softpanorama.org
was initially created as a service to the (now defunct) UN Sustainable Development Networking Programme (SDNP)
without any remuneration. This document is an industrial compilation designed and created exclusively
for educational use and is distributed under the Softpanorama Content License.
Original materials copyright belong
to respective owners. Quotes are made for educational purposes only
in compliance with the fair use doctrine.
FAIR USE NOTICE This site contains
copyrighted material the use of which has not always been specifically
authorized by the copyright owner. We are making such material available
to advance understanding of computer science, IT technology, economic, scientific, and social
issues. We believe this constitutes a 'fair use' of any such
copyrighted material as provided by section 107 of the US Copyright Law according to which
such material can be distributed without profit exclusively for research and educational purposes.
This is a Spartan WHYFF (We Help You For Free)
site written by people for whom English is not a native language. Grammar and spelling errors should
be expected. The site contain some broken links as it develops like a living tree...
Disclaimer:
The statements, views and opinions presented on this web page are those of the author (or
referenced source) and are
not endorsed by, nor do they necessarily reflect, the opinions of the Softpanorama society. We do not warrant the correctness
of the information provided or its fitness for any purpose. The site uses AdSense so you need to be aware of Google privacy policy. You you do not want to be
tracked by Google please disable Javascript for this site. This site is perfectly usable without
Javascript.
Last modified: November, 07, 2020