Blog-based Steganography
Parcially based on Wikipedia article
The word steganography is of Greek origin and means "concealed writing" from the Greek words steganos
(στεγανός) meaning "covered or protected", and graphei (γραφή) meaning "writing". The power of
steganography is reflected in the proverb "To find a needle in a heap of hey" which means almost impossible
task. The key idea is that secret messages are imbedded into "carrier" text. In case of text it is typically
larger then the secret message. Crrie can be in different format too (archive, picture, TCP IP packets,
etc). It is importna that carrier looks like completely "innocent" information: regular
family photos or other images, scholarly articles, shopping lists, private letters or novels. One of
the early methods was to use invisible ink with lines written between the visible lines of a private
letter. In the simplest form milk can be used. It revealed by heating the paper.
Steganography hides the fact of existence of secret message in some open message or a set of message
which can be in any feasible format (including pictures). That provides perfect cover which allow
to exchange of private messages under repressive regimes hell-bend of snooping citizen communications.
it also allow civil protest communications, although here the attention of government probably will
be such that the algorithms will soon be revealed.
There are some basic definition:
- The payload is the data to be covertly communicated.
- The carrier is the signal, stream, or data file into which the payload is hidden; which
differs from the "channel" (typically used to refer to the type of input, such as "a JPEG image")
- The resulting signal, stream, or data file which has the payload encoded into it is sometimes
referred to as the package, stego file, or covert message.
- The encoding density is the percentage of bytes, samples, or other signal elements which
are modified to encode the payload. Commonly it is much less then 1.
Additional terminology
- In a set of files, those files considered likely to contain a payload are called suspects.
- If the suspect was identified through some type of statistical analysis, it might be referred
to as a candidate.
The value of steganography dramatically increased after Snowden revelation. It offer better security
against a non-human adversary such as NSA data connection algorithms,
ECHELON and similar systems then
plain vanilla cryptography. If can be combined with cryptography -- in this case steganography messages
is encrypted or encrypted message is imbedded in steganography set of messages ("carrier").
The first recorded use of the term was in 1499 by Johannes Trithemius in his Steganographia, a treatise
on cryptography and steganography disguised as a book on magic.
The advantage of steganography over cryptography alone is that messages do not attract attention
to themselves. Plainly visible encrypted messages arouse suspicion, and may in themselves be incriminating
in countries where encryption is illegal. Therefore, whereas cryptography protects the contents of a
message, steganography can be said to protect both messages and communicating parties.
Steganographic coding inside of a transport layer, such as a document file, image file, program or
protocol can be arbitrarily complex.
It is not required that the payload is imbedded into a single file. It can be imbedded in multiple
files, so that nothing can be recovered from a single file.
Images and other media files are attractive carrier for steganographic transmission because
of their large size. As a simple example, payload can be put in ignored sections of a file, such as
after the comments of the carrier file written in HTML. or by Making text the same color as the background
in word processor documents and e-mails that are displayed as HTML, PDF or Word Files.
"After Snowden" problem that your email message are no longer private is pretty annoying. Blogs can
be used for exchange of private messages between individuals instead of regular email. Posts or comments
can be fractionalized and the (possibly encrypted) pieces can be added as comments, Javascript
programs on the blog post and/or HTML markup.
As most block allow comments in this case the selection of blogs and the method of hiding the message
is the symmetric key that sender and recipient are shared; the carrier of the hidden message is the
whole blogosphere.
Blog bases steganography can be distributed In this case the payload is split between multiple
carrier files in several different locations. Which make detection of the payload more difficult. see
for example,
U.S. Patent
8,527,779 by cryptographer William Easttom (Chuck Easttom).
Images present interesting opportunities as a carrier of private messages. it is probably the simplest
steganography method that can be used with blogs. The larger the cover message is (in data content terms—number
of bits) relative to the hidden message, the easier it is to hide the latter. For this reason, digital
pictures (which contain large amounts of data) are used to hide messages on the Internet and on other
communication media. It is not clear how commonly this is actually done but there are multiple program
that also to perform this type oftrnasformation of the picture. the obvious drawback is that this
technique is well known and as such easily detectable. But required processing power is considerable.
Requres that each party has its own blog on which it can post images. Most images should be "clean".
Only specially marked should contain payload. Instead of static images a videostream can be used.
For example: a 24-bit bitmap will have 8 bits representing each of the three color values (red, green,
and blue) at each pixel. If we consider just the blue there will be 28 different values of blue. The
difference between 11111111 and 11111110 in the value for blue intensity is likely to be undetectable
by the human eye. Therefore, the least significant bit can be used (more or less undetectably) for something
else other than color information. If we do it with the green and the red as well we can get one letter
of ASCII text for every three pixels.
In the message is encrypted that even detection of the carrier message allow just to retrieve crypto
text.
Stated somewhat more formally, the objective for making steganographic encoding difficult to detect
is to ensure that the changes to the carrier (the original signal) due to the injection of the payload
(the signal to covertly embed) are visually (and ideally, statistically) negligible; that is to say,
the changes are indistinguishable from the noise floor of the carrier. Any
medium can be a carrier, but media with a large amount of redundant or compressible information are
better suited.
From an information theoretical point of view, this means that the channel must have more capacity
than the "surface" signal requires; that is, there must be redundancy. For a digital image, this may
be noise from the imaging element; for digital audio, it may be noise from recording techniques or amplification
equipment. In general, electronics that digitize an analog signal suffer from several noise sources
such as thermal noise, flicker noise, and shot noise. This noise provides enough variation in the captured
digital information that it can be exploited as a noise cover for hidden data. In addition, lossy compression
schemes (such as JPEG) always introduce some error into the decompressed data; it is possible to exploit
this for steganography use as well.
Steganography can be used for digital watermarking, where a message (being simply an identifier
of the device and timestamp) is hidden in an image so that its source can be tracked or verified (for
example, Coded Anti-Piracy), or even just to identify an image (as in the EURion constellation). Some
color printers identify this way each page they print.
Some modern computer printers use steganography, including
HP and
Xerox brand color laser printers.
These printers add tiny yellow dots to each page. The barely-visible dots contain encoded printer
serial numbers and date and time stamps.[23]
When one considers that messages could be encrypted steganographically
in e-mail messages, particularly e-mail spam, the notion of junk e-mail takes on a whole new light.
Coupled with the "chaffing and winnowing" technique, a sender could get messages out
and cover their tracks all at once.
Rumors about terrorists using steganography started first in the daily newspaper USA Today on February
5, 2001 in two articles titled "Terrorist instructions hidden online" and "Terror groups hide behind
Web encryption". In July the same year, an article was titled even more precisely: "Militants wire Web
with links to jihad". A citation from the article: "Lately, al-Qaeda operatives have been sending hundreds
of encrypted messages that have been hidden in files on digital photographs on the auction site eBay.com".
Other media worldwide cited these rumors many times, especially after the terrorist attack of 9/11,
without ever showing proof. The Italian newspaper Corriere della Sera reported that an Al Qaeda cell
which had been captured at the Via Quaranta mosque in Milan had pornographic images on their computers,
and that these images had been used to hide secret messages (although no other Italian paper ever covered
the story). The USA Today articles were written by veteran foreign correspondent Jack Kelley, who
in 2004 was fired after allegations emerged that he had fabricated stories and sources.
In October 2001, the New York Times published an article claiming that al-Qaeda had used steganography
to encode messages into images, and then transported these via e-mail and possibly via USENET to prepare
and execute the September 11, 2001 terrorist attack. The Federal Plan for Cyber Security and Information
Assurance Research and Development,[22] published in April 2006 makes the following statements:
"...immediate concerns also include the use of cyberspace for covert communications,
particularly by terrorists but also by foreign intelligence services; espionage against sensitive
but poorly defended data in government and industry systems; subversion by insiders, including vendors
and contractors; criminal activity, primarily involving fraud and theft of financial or identity
information, by hackers and organized crime groups..." (p. 9–10)
"International interest in R&D for steganography technologies and their commercialization and
application has exploded in recent years. These technologies pose a potential threat to national
security. Because steganography secretly embeds additional, and nearly undetectable, information
content in digital products, the potential for covert dissemination of malicious software, mobile
code, or information is great." (p. 41–42)
"The threat posed by steganography has been documented in numerous intelligence reports." (p.
42)
Moreover, an online "terrorist training manual", the "Technical Mujahid, a Training Manual for Jihadis"
contained a section entitled "Covert Communications and Hiding Secrets Inside Images."[23]
By early 2002, a Cranfield University MSc thesis developed the first practical implementation of
an online real-time Counter Terrorist Steganography Search Engine. This was designed to detect the most
likely image steganography in transit and thereby provide UK Ministry of Defense Intelligence Staff
a realistic approach to "narrowing the field", suggesting that interception capacity was never the difficulty
but rather prioritizing the target media.
In 2010, the Federal Bureau of Investigation revealed that the Russian foreign intelligence service
uses customized steganography software for embedding encrypted text messages inside image files for
certain communications with "illegal agents" (agents under non-diplomatic cover) stationed abroad.
Spam in message forum is a tremendous problem which is extremely difficult to deal automatically.
Spammers usually a very persisted narrow focused on specific theme and can produce multiple variations
of the same message to avoid detection by the spam filter. All those properties increase their value
as a carrier. But it presents an interesting opportunity to to use "stream" of spam messages as a carrier.
In this case "fake" spam messages can be automatically generated.
As messages of the blog can be updates and the sequence of the updates along with history of updates
can represent carrier. That actually include "fake" spam messages too.
If a mirror of the blog of Web site exists, "imperfect" mirror can be used as a carrier. Imperfect
quotes is another variation of the same theme. In this case any other site can be used an "imperfect
mirror".
Developing Aesop language is another was to including payload into carrier. In this case the hidden
meaning of the plain text is radically different from "surface meaning". Detection of such things are
far beyond any power of modern AI and generally is outside computational capabilities of snooping agencies.
In a way they represent much more complex Turing test then traditional Turing test.
The use of Aesop’s language may be viewed upon both in the context of culture and within the specific
framework. The same message may have quite different meanings depending of cultural context and within
the overall framework of social events which happen at the moment of creation of the message or can
be understood based on common social experience of two communicating individuals. For example
"country shift" or 'fable shift" can not be detected with any automatic processing methods.
In other words, it represent "social encoding" of the payload and principal structural
elements of such encoding are far beyond capabilities of modern computers.
In most case cases the hidden meaning of phrasing one’s thoughts involves either
ideas which are contradicting and unacceptable for the political regime in question or ideas which are
common for the whole of mankind. Most often it implies criticism of the given regime.
Any object or life phenomenon may acquire a special symbolic
value in Aesop language and be understood as such
by other recipent. It is common consent that the creation of
symbols is one of the most ancient manifestations of the mental activity of
humans and here essentially a special language is created.
Steganography is used by some modern printers, including HP and Xerox brand color laser printers.
Tiny yellow dots are added to each page. The dots are barely visible and contain encoded printer
serial numbers, as well as date and time stamps.
Digital steganography output may be in the form of printed documents. A message, the plaintext, may
be first encrypted by traditional means, producing a ciphertext. Then, an innocuous covertext
is modified in some way so as to contain the ciphertext, resulting in the stegotext. For example, the
letter size, spacing, typeface, or other characteristics of a covertext can be manipulated to carry
the hidden message. Only a recipient who knows the technique used can recover the message and then decrypt
it. Francis Bacon developed Bacon's cipher as such a technique.
The ciphertext produced by most digital steganography methods, however, is not printable. Traditional
digital methods rely on perturbing noise in the channel file to hide the message, as such, the channel
file must be transmitted to the recipient with no additional noise from the transmission. Printing introduces
much noise in the ciphertext, generally rendering the message unrecoverable. There are techniques that
address this limitation, one notable example is ASCII Art Steganography.
It is possible to use lookalike characters of the usual ASCII set to look normal, while really carrying
extra bits of information. If the text is displayed correctly, there should be no visual difference
from ordinary text. Some systems, however, may display the fonts differently, and the extra information
would be easily spotted.
Alternately, hidden (e.g., control) characters, and redundant use of markup (e.g., empty bold, underline
or italics) can add embedded within a body of text to hide information that wouldn't be visually apparent
when displayed, but can be discovered by examining the document source.
HTML pages can contain code for extra blank spaces and tabs at the end of lines, as well as different
colors, fonts and sizes, which will not be visible when displayed. A more trivial example is white text
on a white background, which can be revealed by "selecting".
One such method is based on the non-printing Unicode characters Zero-Width Joiner (ZWJ) and Zero-Width
Non-Joiner (ZWNJ).[18] These characters are used for joining and disjoining letters in Arabic, but can
be used in Roman alphabets for hiding information because they have no meaning in Roman alphabets, and
because they are "zero-width" and thus not displayed. The embedding of ZWJ in the cover-text represents
“1” and the embedding of ZWNJ represents “0”. Groups of characters can be used to represent the letters
A (giving it the code “0”, and thus represented by ZWNJ) to Z (giving it the code “1011”, and thus represented
by ZWJ,ZWNJ,ZWJ,ZWJ). These character groups can be inserted between each character of the cover-text,
thereby hiding a message.
Steganography can be more subtle that just hiding message. It can be just obscuring the "spectrum
of the signal", for example frequency of letters in English text. One simple way to obscure frequency
of letters in English text is to inserting random first bits or letters into the plain text before encryption.
Among some approaches:
- Mimic functions convert one file to have the statistical profile of another. This can
thwart statistical methods that help brute-force attacks identify the right solution in a ciphertext-only
attack.
- Messages can be concealed in tampered executable files, exploiting redundancy in the
targeted instruction set.
- Pictures embedded in video material (optionally played at slower or faster speed).
- Injecting imperceptible delays to packets sent over the network from the keyboard. Delays in
keypresses in some applications (telnet or remote desktop software) can mean a delay in packets,
and the delays in the packets can be used to encode data.
- Changing the order of elements in a set.
Detection of physical steganography is tremendously more difficult the detection of of crypto text.
In this case the key unknown is what constitutes the carrier. Especailly in digital age where volumes
of transmitted information are huge this amount to the attempt to fight the needle in a heap of hey.
For example if the suspicion is that paper is the carrier, detection requires careful and complex
physical examination, including the use of magnification, chemical analysis, ultraviolet light, etc.
It is an expecsive and very time-consuming process with obvious resource implications.
However, in the past it was feasible to screen mail of certain suspected individuals or institutions,
such as prisons or prisoner-of-war (POW) camps. During World War II, a technology used to ease monitoring
of POW mail was specially treated paper that would reveal invisible ink. An article in the June 24,
1948 issue of Paper Trade Journal by the Technical Director of the United States Government Printing
Office, Morris S. Kantrowitz, describes in general terms the development of this paper, three prototypes
of which were named Sensicoat, Anilith, and Coatalith paper. These were for the manufacture of post
cards and stationery to be given to German prisoners of war in the US and Canada.
If POWs tried to write a hidden message the special paper would render it visible. At least two US
patents were granted related to this technology, one to Mr. Kantrowitz, No. 2,515,232, "Water-Detecting
paper and Water-Detecting Coating Composition Therefor", patented July 18, 1950, and an earlier one,
"Moisture-Sensitive Paper and the Manufacture Thereof", No. 2,445,586, patented July 20, 1948. A similar
strategy is to issue prisoners with writing paper ruled with a water-soluble ink that "runs" when in
contact with a water-based invisible ink.
In computing, detection of steganographically encoded packages is called steganalysis. The simplest
method to detect modified files, however, is to compare them to known originals, which is possible in
case the picture is in public domain. For example, to detect information being moved through the
graphics on a website, an analyst can maintain known-clean copies of these materials and compare them
against the current contents of the site. The differences, assuming the carrier is the same, will compose
the payload.
In general, using extremely high compression rate makes steganography difficult, but not impossible.
While compression errors provide a hiding place for data, high compression reduces the amount of data
available to hide the payload in, raising the encoding density and facilitating easier detection (in
the extreme case, even by casual observation).
Steganography has been widely used, including in recent historical times and the present day. Possible
permutations are endless and known examples include:
- Hidden messages within wax tablets — The first recorded uses of steganography can be traced
back to 440 BC when Herodotus mentions two examples of steganography in his Histories.[2] Demaratus
sent a warning about a forthcoming attack to Greece by writing it directly on the wooden backing
of a wax tablet before applying its beeswax surface. Wax tablets were in common use then as reusable
writing surfaces, sometimes used for shorthand.
- Hidden messages on messenger's body — also used in ancient Greece. Herodotus tells the
story of a message tattooed on the shaved head of a slave of Histiaeus, hidden by the hair that afterwards
grew over it, and exposed by shaving the head again. The message allegedly carried a warning to Greece
about Persian invasion plans. This method has obvious drawbacks, such as delayed transmission while
waiting for the slave's hair to grow, and the restrictions on the number and size of messages that
can be encoded on one person's scalp.
- In his work "Polygraphiae" Johannes Trithemius developed his so-called
"Ave-Maria-Cipher" with which one can hide information in a Latin praise of God. "Auctor
Sapientissimus Conseruans Angelica Deferat Nobis Charitas Potentissimi Creatoris" for example contains
the concealed word VICIPEDIA.[3]
- In the early days of the printing press, it was common to mix different typefaces on a printed
page due to the printer not having enough copies of some letters otherwise. Because of this, a message
could be hidden using 2 (or more) different typefaces, such as normal or italic, on a page of type.
- During World War II, the French Resistance sent some messages written on the backs of couriers
using invisible ink.
- Hidden messages on paper written in secret inks, under other messages or on the blank
parts of other messages.
- Messages written in Morse code on knitting yarn and then knitted into a piece of clothing
worn by a courier.
- Jeremiah Denton repeatedly blinked his eyes in Morse Code during the 1966 televised press
conference that he was forced into as an American POW by his North Vietnamese captors, spelling out
the word, "T-O-R-T-U-R-E". This confirmed for the first time to the U.S. Military (naval intelligence)
and Americans that American POW's were being tortured in North Vietnam.
- Messages written on envelopes in the area covered by postage stamps.
- During and after World War II, espionage agents used photographically produced microdots to
send information back and forth. Microdots were typically minute, approximately less than the size
of the period produced by a typewriter. World War II microdots needed to be embedded in the paper
and covered with an adhesive, such as collodion. This was reflective and thus detectable by viewing
against glancing light. Alternative techniques included inserting microdots into slits cut into
the edge of post cards.
- During WWII, Velvalee Dickinson, a spy for Japan in New York City, sent information to accommodation
addresses in neutral South America. She was a dealer in dolls, and her letters discussed the
quantity and type of doll to ship. The stegotext was the doll orders, while the concealed "plaintext"
was itself encoded and gave information about ship movements, etc. Her case became somewhat famous
and she became known as the Doll Woman.
- In 1968, crew members of the USS Pueblo intelligence ship held as prisoners by North Korea, communicated
in sign language during staged photo opportunities, informing the United States they were not defectors,
but were captives of the North Koreans. In other photos presented to the US, crew members gave "the
finger" to the unsuspecting North Koreans, in an attempt to discredit photos that showed them smiling
and comfortable.
Modern steganography entered the world in 1985 with the advent of the personal computer being applied
to classical steganography problems. Development following that was slow, but has since taken off, going
by the number of "stego" programs available. Early examples included:
- Concealing messages within the lowest bits of noisy images or sound files.
- Concealing data within encrypted data or within random data. The data to be concealed are first
encrypted before being used to overwrite part of a much larger block of encrypted data or a block
of random data (an unbreakable cipher like the one-time pad generates ciphertexts that look
perfectly random if one does not have the private key).
- Conceling text within image files.
Notable quotes:
"... However, he adds, "I hope that folks think about their operational security and also about how journalists can protect themselves – and their sources as well." ..."
They're almost invisible but contain a hidden code – and their presence on a leaked
document has sparked speculation about their usefulness to FBI investigators. BBC Future |
On 3 June, 2017, FBI agents arrived at the house of government contractor Reality Leigh
Winner in Augusta, Georgia. They had spent the last two days investigating a top secret classified
document that had allegedly been leaked to the pres s. In order to track down Winner,
agents claim they had carefully studied copies of the document provided by online news site The
Intercept and noticed creases suggesting that the pages had been printed and "hand-carried out
of a secured space".
In
an affidavit , the FBI alleges that Winner admitted printing the National Security Agency
(NSA) report and sending it to The Intercept. Shortly after a story about the leak was
published, charges against Winner were made public.
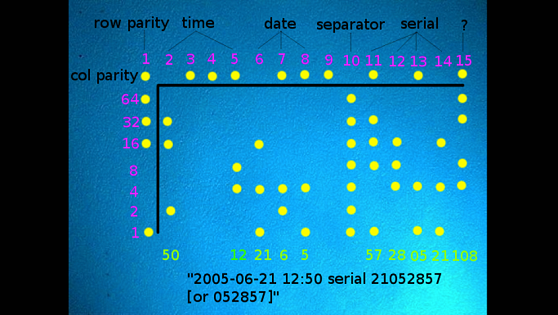
At that point, experts began taking a closer look at the document, now publicly available on
the web. They discovered something else of interest: yellow dots in a roughly rectangular
pattern repeated throughout the page. They were barely visible to the naked eye, but formed a
coded design. After some quick analysis , they
seemed to reveal the exact date and time that the pages in question were printed: 06:20 on 9
May, 2017 – at least, this is likely to be the time on the printer's internal clock at
that moment. The dots also encode a serial number for the printer.
These "microdots" are well known to security researchers and civil liberties campaigners.
Many colour printers add them to documents without people ever knowing they're
there.

Dots from a HP Laserjet printer, illuminated with blue light. Credit: Florian
Heise/Wikipedia .
In this case, the FBI has not said publicly that these microdots were used to help identify
their suspect, and the bureau declined to comment for this article. The US Department of
Justice, which published news of the charges against Winner, also declined to provide further
clarification.
In a
statement , The Intercept said, "Winner faces allegations that have not been proven. The
same is true of the FBI's claims about how it came to arrest Winner."
But the presence of microdots on what is now a high-profile document (against the NSA's
wishes) has sparked great interest.
"Zooming in on the document, they were pretty obvious," says Ted Han at cataloguing platform
Document Cloud , who was one of
the first to notice them. "It is interesting and notable that this stuff is out there."
Another observer was security researcher Rob Graham, who published a blog
post explaining how to identify and decode the dots. Based on their positions when plotted
against a grid, they denote specific hours, minutes, dates and numbers. Several security
experts who decoded the dots came up with the same print time and date.
Microdots have existed for many years. The Electronic Frontier Foundation (EFF) maintains a
list of colour printers
known to use them . The images below, captured by the EFF, demonstrate how to decode
them:
These yellow dots, magnified 60 times, were found on a Xerox printout. Credit: Electronic
Frontier Foundation/CC BY 3.0 .
The dots become more easily visible when magnified and photographed under a blue LED
flashlight. Credit: Electronic Frontier Foundation/CC BY 3.0 .
For further clarity, the dots here are annotated. So what does the shape mean? Credit:
Electronic Frontier Foundation/CC BY 3.0 .
The position of the dots reveals the time and date of the printout, and the serial number
of the device. Credit: Electronic Frontier Foundation/CC BY 3.0 .
As well as perhaps being of interest to spies, microdots have other potential uses, says Tim
Bennett, a data analyst at software consultancy Vector 5 who also examined the allegedly leaked
NSA document.
"People could use this to check for forgeries," he explains. "If they get a document and
someone says it's from 2005, [the microdots might reveal] it's from the last several
months."
If you do encounter microdots on a document at some point, the EFF has an online tool that should
reveal what information the pattern encodes.
Hidden Messages
Similar kinds of steganography – secret messages hidden in plain sight – have
been around for much longer.
Slightly more famously, many banknotes around the world feature a peculiar
five-point pattern called the Eurion constellation . In an effort to avoid counterfeiting,
many photocopiers and scanners are programmed not to produce copies of the banknotes when this
pattern is recognised.
The NSA itself points to a fascinating historical example of tiny dots forming messages
– from World War Two. German spies in Mexico were found to have taped
tiny dots inside the envelope concealing a memo for contacts in Lisbon.
At the time, these spies were operating undercover and were
trying to get materials from Germany , such as radio equipment and secret ink. The Allies
intercepted these messages, however, and disrupted the mission. The tiny dots used by the
Germans were often simply bits of unencrypted text miniaturised to the size of a full-stop.
This sort of communication was widely used during WWII and afterwards, notably during the
Cold War. There are reports of agents operating for the Soviet Union, but based undercover in
West Germany and
using letter drops to transmit these messages .
Microdots taped inside the label of an envelope sent by German spies in Mexico City to
Lisbon during World War Two. Credit: Wikipedia .
And today, anyone can try using microtext to protect their property – some companies,
such as Alpha Dot in the UK , sell
little vials of permanent adhesive full of pin-head sized dots, which are covered in
microscopic text containing a unique serial number. If the police recover a stolen item, the
number can in theory be used to match it with its owner.
Many examples of these miniature messages do not involve a coded pattern as with the output
of many colour printers, but they remain good examples of how miniscule dispatches physically
applied to documents or objects can leave an identifying trail.
Some forms of text-based steganography don't even use alphanumeric characters or symbols at
all. Alan Woodward, a security expert at the University of Surrey, notes the example of 'Snow'
– Steganographic Nature Of Whitespace – which places spaces and tabs at the end of
lines in a piece of text. The particular number and order of these white spaces can be used to
encode an invisible message.
"Locating trailing whitespace in text is like finding a polar bear in a snowstorm,"
the Snow website explains .
Woodward points out, though, that there are usually multiple ways of tracing documents back
to whoever printed or accessed them.
"Organisations such as the NSA have logs of every time something is printed, not just
methods of tracking paper once printed," he says. "They know that people know about the yellow
dots and so they don't rely upon it for traceability."
There is a long-running debate over whether it is ethical for printers to be attaching this
information to documents without users knowing. In fact, there has even been a suggestion that
it is a
violation of human rights and one MIT
project has tracked more than 45,000 complaints to printer companies about the
technology.
Still, many believe that the use of covert measures to ensure the secrecy of classified
documents remains necessary in some cases.
"There are things that governments should be able to keep secret," says Ted Han.
However, he adds, "I hope that folks think about their operational security and also about
how journalists can protect themselves – and their sources as well."
I doubt that this is promising as described, but something along those lines (with predefined set
of equivalencies) can be developed further. Consider instructions equivalencies as some kind of bit
mask that can be applied to any of the program strings
Netizens with extreme privacy needs got a new tool for their cyber utility belts recently with
the release of an application that lets users hide secret messages in virtually any executable computer
program, without changing the program's size or affecting its operation.
The tool is called "Hydan," an old English word for the act of hiding something, and it's part
of a research project by Columbia University computer science masters student Rakan El-Khalil, who
showed off the program to a small group of open-source programmers and hackers gathered at the second
annual CodeCon conference in San Francisco on Sunday.
Hydan is a novel development in the field of steganography -- the science of burying secret
messages in seemingly innocuous content. Popular stego programs operate on image and music
files, where a secret missive can be hidden without altering the content enough to be perceived by
human senses. But because they contain instructions for a computer's processor, executable files
are less forgiving of tampering. Improperly changing a single bit of executable code can render an
application completely unusable.
El-Khalil's research focused on redundancies in the Intel x86 instruction set -- places
where at least two different instructions are effectively the same. Each choice between two
redundant options can represent a single bit of data. "The problem with program binaries is there
is just not a lot of redundancy in them," said El-Khalil.
He found some of that useful redundancy in the instructions that tell the computer to add or subtract.
A computer instruction to add the number 50 to another value, for example, can be replaced with
an instruction to subtract the number -50 instead. Mathematically, the instructions are the same.
In choosing between the two, a stego program can get one bit of covert storage out of each addition
or subtraction operation in the executable -- without changing the way the application runs, or adding
a single byte to its size. "If we use a scenario in which addition is zero, and subtraction is one,
we can just go through and flip them as needed," El-Khalil explained.
El-Khalil concedes that the method is imperfect -- an application that's been impressed
with a secret message has considerably more "negative subtractions" than an unadulterated program,
making it easy to pick out through a statistical analysis. Hydan could also break programs
that are self-modifying or employ other unconventional techniques. And it's less efficient than stego
programs for image and sound files: good steganography for a JPEG file can hide one byte of storage
in 17 bytes of image, while Hydan's ratio is one byte of storage to 150 bytes of code.
Future versions of Hydan
will boost that capacity by finding different places to code data, such as in the order of a program's
functions, and the order in which arguments are passed to those functions. For now, the application
is still powerful enough to secretly stash the United States Constitution and the Declaration of
Independence in a single copy of Microsoft Word.
Beyond the covert uses, the technology could be used to attach a digital signature to an application,
or to embed an executable with a virtual watermark.
Softpanorama Recommended
Papers
CHACS
Publications for 2002 Moskowitz, Ira S., Neil F. Johnson, and Michael Jacobs, "A Detection Study
of an NRL Steganographic Method", NRL/MR/554002-8635, August 16, 2002.
PDF
For a bound, easier to read, copy of this please contact:
Ms. L. Norton, Library---Code 5225, NRL, Washington, DC 20375
In this report we analyze in detail a method of image steganography developed by NRL. Our conclusion
is that this method of steganography is undetectable by current pragmatic statistical stego detection
techniques, primarily because it alters a very small number of pixels. The small size of the
embedded message is the key to the lack of detection, provided that a non-anomalous cover image
is used.
Newman, Richard E., Ira S. Moskowitz, LiWu Chang, and Murali M. Brahmadesam, "A Steganographic
Embedding Undetectable by JPEG Compatibility Steganalysis", Proc. Information Hiding 2002, 7-9 October
2002, (final proceedings will be published by Springer, LNCS series, ed. F.A.P. Petitcolas).
PDF
Steganography and steganalysis of digital images is a cat-and-mouse game. In recent work, Fridrich,
Goljan and Du introduced a method that is surprisingly accurate at determining if bitmap images
that originated as JPEG files have been altered (and even specifying where and how they were altered),
even if only a single bit has been changed. However, steganographic embeddings that encode embedded
data in the JPEG coefficients are not detectable by their JPEG compatibility steganalysis.
This paper describes a steganographic method that encodes the embedded data in the spatial domain,
yet cannot be detected by their steganalysis mechanism. Furthermore, we claim that our method
can also be used as a steganographic method on files stored in JPEG format. The method described
herein uses a novel, topological approach to embedding. The paper also outlines some extensions
to the proposed embedding method.
Moskowitz, Ira S., Garth E. Longdon and LiWu Chang, "A New Paradigm Hidden in Steganography".
Proceedings, New Security Paradigms Workshop, Sept. 2000, Ballycotton, Co. Cork, Ireland. Also appears
in "The Privacy Papers," ed. R. Herold, Auerbach Press, 2001.
PostScript,
PDF
We discuss how steganography, in contrast to similar disciplines, requires a new paradigm based
upon discontinuities and the absence of noise as a detection deterrent.
Links
CHACS
Publications for 2002 Moskowitz, Ira S., Neil F. Johnson, and Michael Jacobs, "A Detection Study
of an NRL Steganographic Method", NRL/MR/554002-8635, August 16, 2002.
PDF
For a bound, easier to read, copy of this please contact:
Ms. L. Norton, Library---Code 5225, NRL, Washington, DC 20375
In this report we analyze in detail a method of image steganography developed by NRL. Our conclusion
is that this method of steganography is undetectable by current pragmatic statistical stego detection
techniques, primarily because it alters a very small number of pixels. The small size of the embedded
message is the key to the lack of detection, provided that a non-anomalous cover image is used.
Newman, Richard E., Ira S. Moskowitz, LiWu Chang, and Murali M. Brahmadesam, "A Steganographic Embedding
Undetectable by JPEG Compatibility Steganalysis", Proc. Information Hiding 2002, 7-9 October 2002, (final
proceedings will be published by Springer, LNCS series, ed. F.A.P. Petitcolas).
PDF
Steganography and steganalysis of digital images is a cat-and-mouse game. In recent work, Fridrich,
Goljan and Du introduced a method that is surprisingly accurate at determining if bitmap images that
originated as JPEG files have been altered (and even specifying where and how they were altered),
even if only a single bit has been changed. However, steganographic embeddings that encode embedded
data in the JPEG coefficients are not detectable by their JPEG compatibility steganalysis. This paper
describes a steganographic method that encodes the embedded data in the spatial domain, yet cannot
be detected by their steganalysis mechanism. Furthermore, we claim that our method can also be used
as a steganographic method on files stored in JPEG format. The method described herein uses a novel,
topological approach to embedding. The paper also outlines some extensions to the proposed embedding
method.
Moskowitz, Ira S., Garth E. Longdon and LiWu Chang, "A New Paradigm Hidden in Steganography". Proceedings,
New Security Paradigms Workshop, Sept. 2000, Ballycotton, Co. Cork, Ireland. Also appears in "The Privacy
Papers," ed. R. Herold, Auerbach Press, 2001.
PostScript,
PDF
We discuss how steganography, in contrast to similar disciplines, requires a new paradigm based
upon discontinuities and the absence of noise as a detection deterrent.

